Deconstructing the 4-Way Handshake
What is the 4-Way Handshake?
The 4-way handshake is a series of 4 EAPoL-Key frames that are used between a supplicant and authenticator station to validate compatible cipher suite selection and to facilitate the creation and installation of encryption keys. It is the final stage in the association process and establishes a Robust Security Network (RSN) Association (RSNA), finally allowing for secure transmission of client data traffic.
Inputs
- Authenticator and Supplicant MAC Addresses
- Pairwise Master Key (PMK)
- Group Master Key (GMK)
- RSN Information Element (RSNIE)
The authenticator and supplicant know each others’ MAC addresses because they are included in the MAC header of every frame exchange between them.
The PMK is derived from the Master Session Key (MSK) which is a product of the 802.1X authentication. A new 802.1X authentication would generate a new MSK and thus a new PMK.
For PSK authentication, the PMK is the PSK and so therefore does not change unless the passphrase/PSK changes.
The GMK is generated by the authenticator.
The RSNIE carries information about a station’s authentication and encryption capabilities, including cipher suite information.
Byproducts
- Authenticator and Supplicant Nonces (ANonce and SNonce)
- Message Integrity Code / Check (MIC)
A nonce, as it pertains to cryptography, is a random/arbitrary number that is used on a one-time basis, typically as an input to some cryptographic algorithm. The authenticator and supplicant each generate a nonce known as the ANonce and SNonce respectively.
MICs are generated to validate the integrity of the transmission.
Final Products
- Pairwise Transient Key (PTK)
- Group Temporal Key (GTK)
The PTK is used to encrypt unicast transmissions. It is derived from a function involving the PMK, ANonce, SNonce, the authenticator’s MAC address, and the supplicant’s MAC address.
The GTK is used to encrypt broadcast and multicast transmissions.
The Process
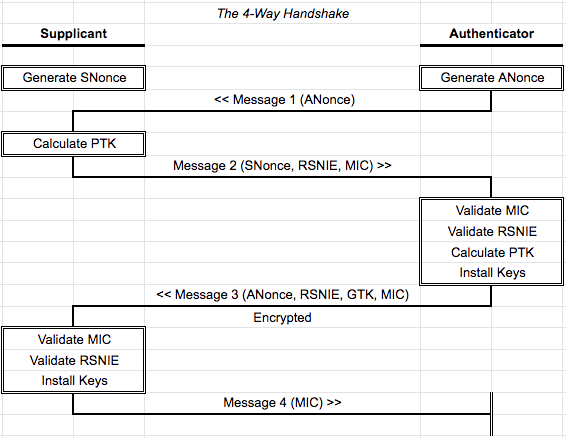
- Generate Nonces
- Message 1
- Calculate PTK
- Message 2
- Validate MIC and RSNIE, Calculate PTK, Install Keys
- Message 3
- Validate MIC and RSNIE, Install Keys
- Message 4
Generate Nonces
The authenticator and supplicant each generate a nonce known as the ANonce and SNonce respectively.
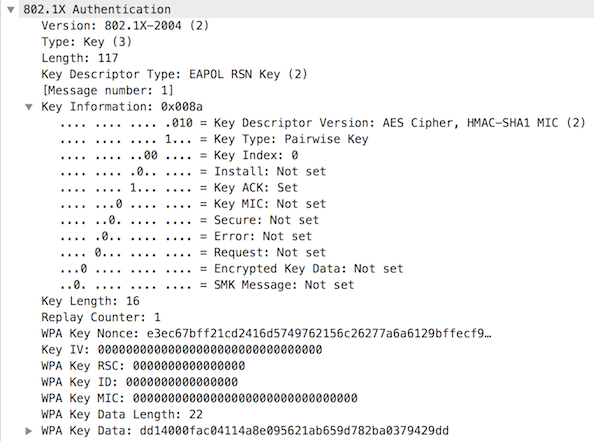
Message 1
The authenticator sends the ANonce to the supplicant station. This is the only message in the sequence without a MIC.
Calculate PTK
The supplicant already has its own and the authenticator’s MAC addresses and the PMK. It has also already generated its SNonce. Once it receives the ANonce from the authenticator through Message 1, it uses all of these inputs to generate the PTK.
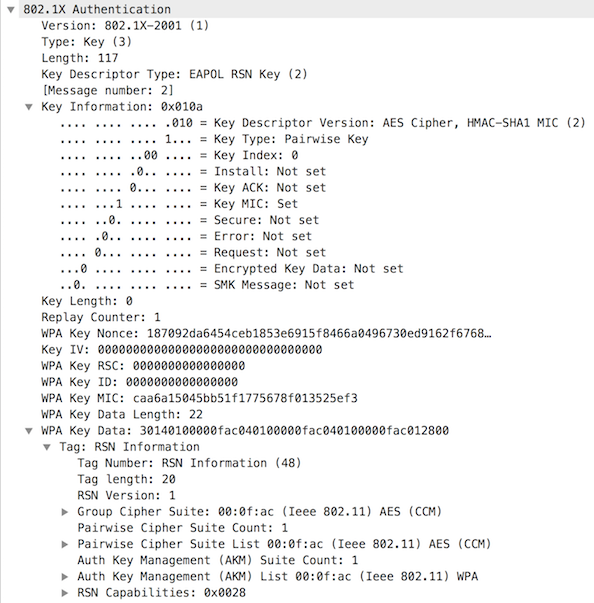
Message 2
The supplicant sends the SNonce, RSNIE, and MIC to the authenticator station.
Validate MIC and RSNIE, Calculate PTK, Install Keys
The authenticator validates the MIC as well as the RSNIE with its own capabilities.
The authenticator already has its own and the supplicant’s MAC addresses and the PMK. It has also already generated its ANonce. Once it receives the SNonce from the supplicant through Message 2, it uses all of these inputs to generate and install the PTK.
If the GTK doesn’t already exist, for example, from a previous authentication, the authenticator also generates a GTK from the GMK and installs it.
Message 3
The authenticator sends the ANonce, RSNIE, GTK, MIC, and instruction to install both the PTK and GTK to the supplicant. This message is encrypted by the PTK and it is the only encrypted message in the sequence.
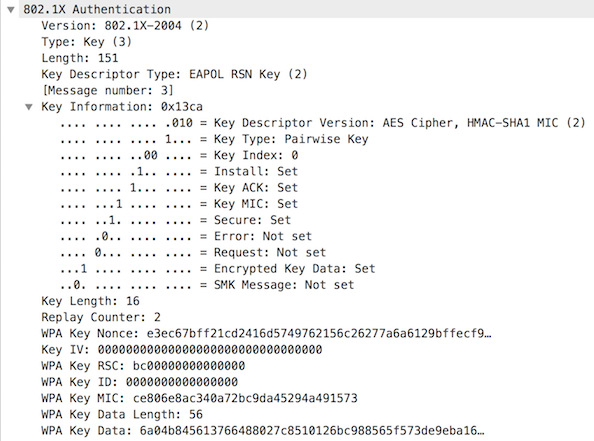
Validate MIC and RSNIE, Install Keys
The supplicant validates the MIC as well as the RSNIE with its own capabilities.
The supplicant then installs the PTK and GTK.
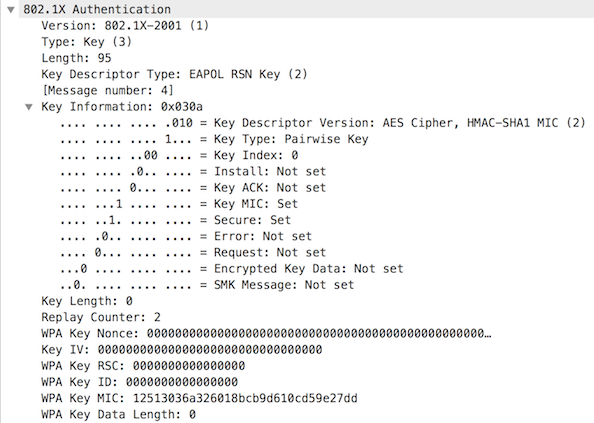
Message 4
The supplicant sends a MIC to the authenticator. This message is to notify the authenticator that the keys have been successfully installed. Transmission of client data traffic may now commence.
Quick Tips
| Message 1 | Message 2 | Message 3 | Message 4 | |
| Direction | A > S | S > A | A > S | S > A |
| Nonce | A | S | A | |
| MIC | X | X | X | |
| Install | X | |||
| GTK | X | |||
| Encrypted | X |
- Message 1 is the only one without a MIC
- Message 3 is includes the GTK and instruction to install keys
- Message 3 is the only one that is encrypted
- Message 4 is the only one without a nonce
References
- CWAP Certified Wireless Analysis Professional: Official Study Guide by Ben Miller, Peter Mackenzie, David D. Coleman, and David A. Wescott
- CWSP Certified Wireless Security Professional Study Guide by Bryan E. Harkins, David A. Wescott, and David D. Coleman
- Wi-Fi security – WEP, WPA, and WPA2 by Guillaume Lehembre
Good breakdown of the 4-way handshake. Did you get a wireless capture for this information?
Thanks! Yes, it’s not hard to do =) Huge thanks to demo by Phil Morgan at NC-Expert and the exercises in the Sybex books!