WPA (Wi-Fi Protected Access) was designed to be an immediate patch to the failings of WEP (Wired Equivalent Privacy) without demanding hardware changes in devices that already ran on WEP. Hence WPA also uses the TKIP encryption algorithm, similar to WEP. WPA2 uses the AES-CCMP algorithm for encryption, which is more powerful and robust compared to TKIP. Both WPA and WPA2 are vulnerable to dictionary attacks, to execute which one needs the four-way WPA handshake between the client and the access point and a dictionary that must contain the passphrase.
The Four-Way Handshake
WPA/ WPA2 PSK works by basically deriving a per-session key, called Pair-wise Transient Key (PTK), that is derived from the following factors:
- Pre-Shared Key (PSK) / Pair-wise Master Key (PMK)
- SSID of Network
- Authenticator (AP) Nonce (ANonce)
- Supplicant (client) Nonce (SNonce)
- Authenticator (AP) MAC address
- Supplicant (client) MAC address
A nonce is a term used in cryptography to denote a random or pseudo-randomly generated number used only once in a cryptographic communication.
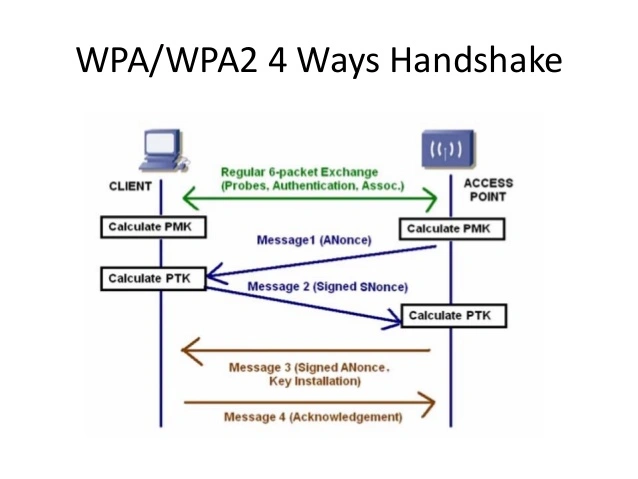
Putting the PMK aside for later consideration, any attacker has 4 of the remaining 5 factors (SSID, Supplicant Nonce and both MAC addresses (by simple sniffing)). The fifth factor (ANonce) the attacker can retrieve by simple sniffing. The only thing the attacker does not have is the Pre-Shared Key. The Pre-Shared Key is derived by using the passphrase entered by the client and the SSID of the network. The combination of both is sent through the Password-Based Key Derivation Function (PBKDF2) which outputs a 256 bit shared key (Pair-wise Master Key). A Pseudo-Random Function (PRF) takes the PSK, ANonce, SNonce and both the MAC addresses to generate a transient (temporary key). Since this temporary key is used to encypt communication, the PMK cannot be derived by any attack on the traffic and the PTK cannot be changed unless the passphrase itself is changed.
Let’s now look into the first 2 messages before looking at where the dictionary attack works:
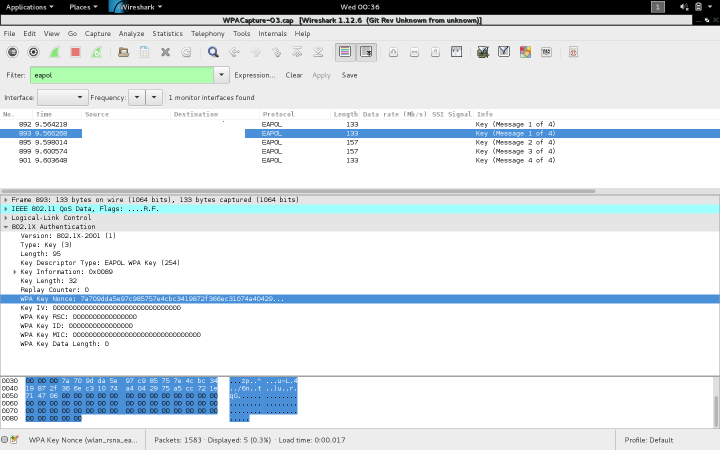
EAP(Extensible Authentication Protocol) message 1: The first message as shown in the figure comes from the AP containing a random number as nonce. Since this message contains all that is required for the client to calculate the PTK (ANonce and Authenticator MAC)
EAP Message 2: As the client replies to the first message sent by the AP, it sends the used SNonce to the AP , and also an encrypted version of the SNonce protected by a cryptographic hash called Message Integrity Code (MIC). The cipher used in this hash is also mentioned in the message.
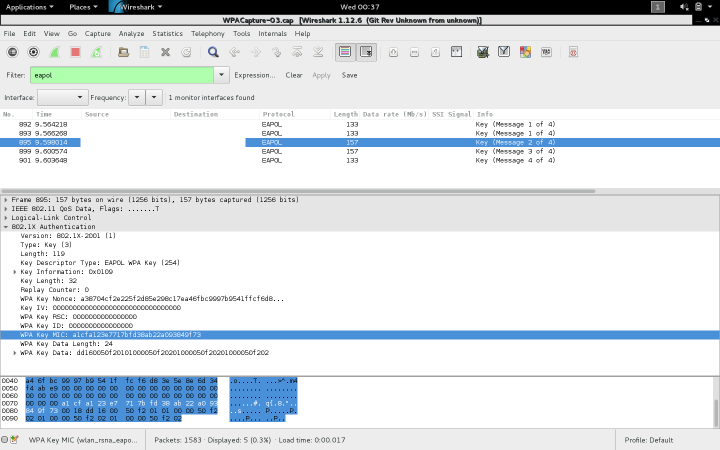
As we can see above , the message 2 contains a MIC that is to be verified using the PTK. If the value that we get by using the hashing algorithm specified and hashing the SNonce with the correct PTK, the value in the MIC should match. This is where a brute-force approach for the dictionary attack works. We know the cryptographic hash functions to calculate the PMK and PTK and the inputs to each of them (passphrase + SSID for PMK and PMK+AMac+SMac+SNonce+ANonce for PTK). The passphrase is a simple 8-63 character combination of numbers, the alphabet and special chars. This is what is read in from the dictionary. Assuming the passphrase exists in the dictionary, the PMK generated will in turn generate the proper PTK, which is tested with the MIC to verify the validity of the key.

