exploring sshd-keygen-wrapper on Mac
The sshd-keygen-wrapper tool, located within macOS Privacy settings, has garnered attention from users, particularly when they discover it in the Full Disk Access section of their Privacy preferences. While its presence might be disconcerting to some, a deeper understanding of its purpose and functionality can dispel any concerns.
The inclusion of sshd-keygen-wrapper in the Full Disk Access section can be perplexing. Some users may interpret it as an indication of a security compromise or malware. However, the reality is that sshd-keygen-wrapper is an integral component of macOS, functioning as an SSH secure shell key generator. Its primary role is to facilitate users in enabling or disabling remote access to their Mac via the Secure Shell Protocol (SSH).
The visibility of sshd-keygen-wrapper in Full Disk Access correlates with the Remote Login setting. Users who have never activated Remote Login will not encounter this tool. But for those who have, the tool will be present, albeit disabled by default, indicating that its access and permissions are inactive.
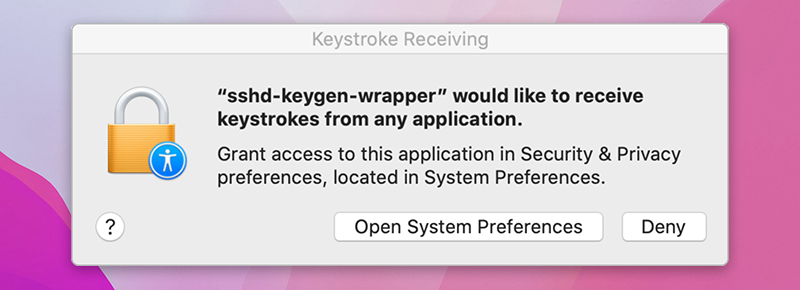
While navigating the Privacy settings on a Mac, users might come across a popup message stating, “‘sshd-keygen-wrapper’ would like to receive keystrokes from any application.” This message can be particularly perplexing, leading to concerns about the tool’s intentions and whether it poses any security risks.
Is it malware?
A prevalent misconception is associating sshd-keygen-wrapper with malware or unwanted software. Contrary to this belief, the tool is an authentic part of macOS and poses no malicious intent. Its placement in the Full Disk Access section is inherently tied to the SSH remote access feature. Activating SSH remote access from System Preferences ensures the association of sshd-keygen-wrapper, which then guarantees the generation of secure SSH shell keys for remote connections.
Should sshd-keygen-wrapper be granted Full Disk Access?
A frequently posed question revolves around whether sshd-keygen-wrapper should receive full disk access. Users contemplating remote access to their Mac via SSH might consider this option. By granting Full Disk Access to sshd-keygen-wrapper, macOS inherently extends the same privilege to SSH. As a result, any individual accessing the Mac through SSH can access all data, encompassing emails, messages, and files. The choice to activate this feature should stem from individual security assessments and requirements.

Procedure to remove sshd-keygen-wrapper from Privacy preferences
For users inclined to eliminate sshd-keygen-wrapper from the Privacy preferences, the steps are as follows:
- Navigate to Apple menu > System Preferences > Security & Privacy > Privacy.
- Choose Full Disk Access. Note: This section may be locked. Click the Lock icon to unlock and input the Mac user password.
- Select sshd-keygen-wrapper and press the (–) Remove button.
It’s imperative to acknowledge that reactivating Remote Login will reintroduce sshd-keygen-wrapper to the list.
Interlinking with other Mac processes
Comprehending sshd-keygen-wrapper necessitates an understanding of the broader macOS landscape. Several pivotal processes underpin the system’s functionality:
- windowserver: Entrusted with the management of macOS’s GUI, it governs all visual elements on the screen, spanning from window operations to animations.
- kernel_task: As the cornerstone of the macOS operating system, it diligently oversees system resources, ensuring the uninterrupted functioning of applications and processes.
- launchd: This inaugural process activates when macOS boots up. It lays the groundwork for the system environment and initiates other processes, marking its significance in system booting and administration.
- Dock: True to its name, this process supervises the Mac’s Dock, guaranteeing the fluid operation, visual appeal, and user interaction of the encapsulated application icons.
In conclusion, while sshd-keygen-wrapper may appear as an enigma on macOS initially, its pivotal role in orchestrating remote access and safeguarding user privacy cannot be understated. A comprehensive grasp of its function and purpose empowers users to make well-informed decisions regarding its permissions.
Posted on September 8, 2019, in Mac, Security-2 and tagged Full Disk Access, how to, Mac, MacOS, malware, Privacy, processes, security, SSH. Bookmark the permalink. Leave a comment.

Leave a comment
Comments 0