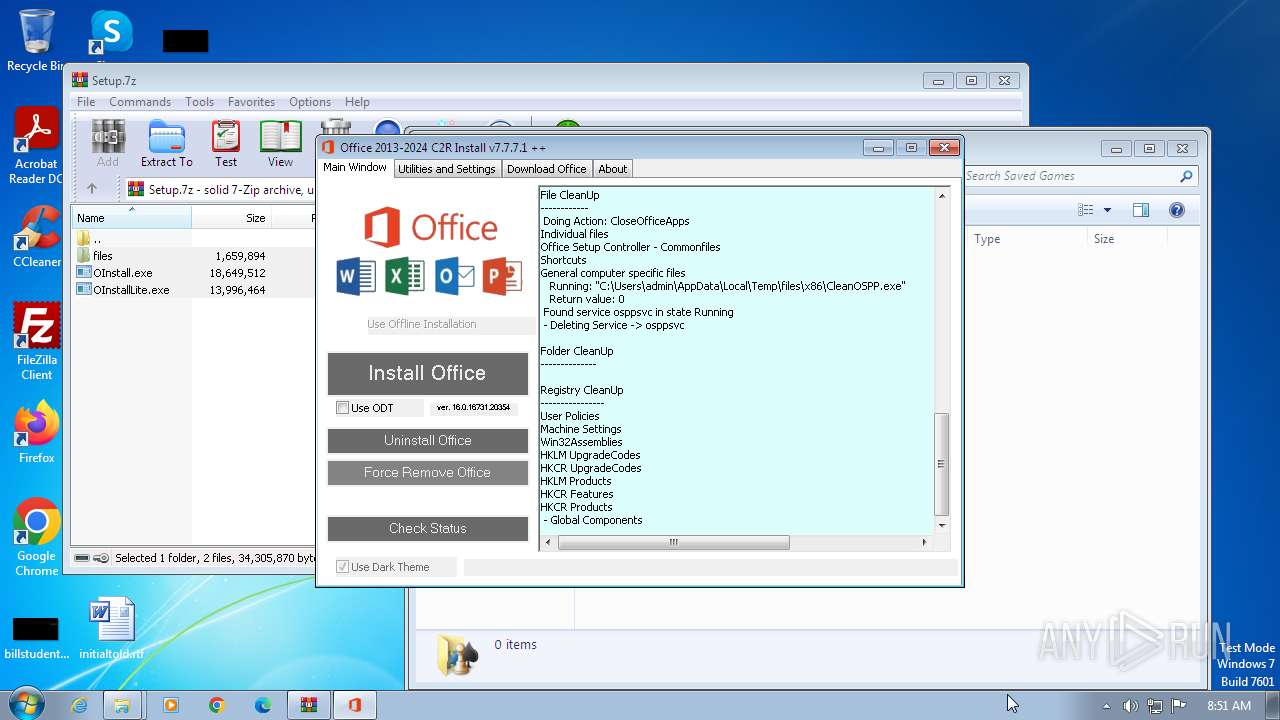
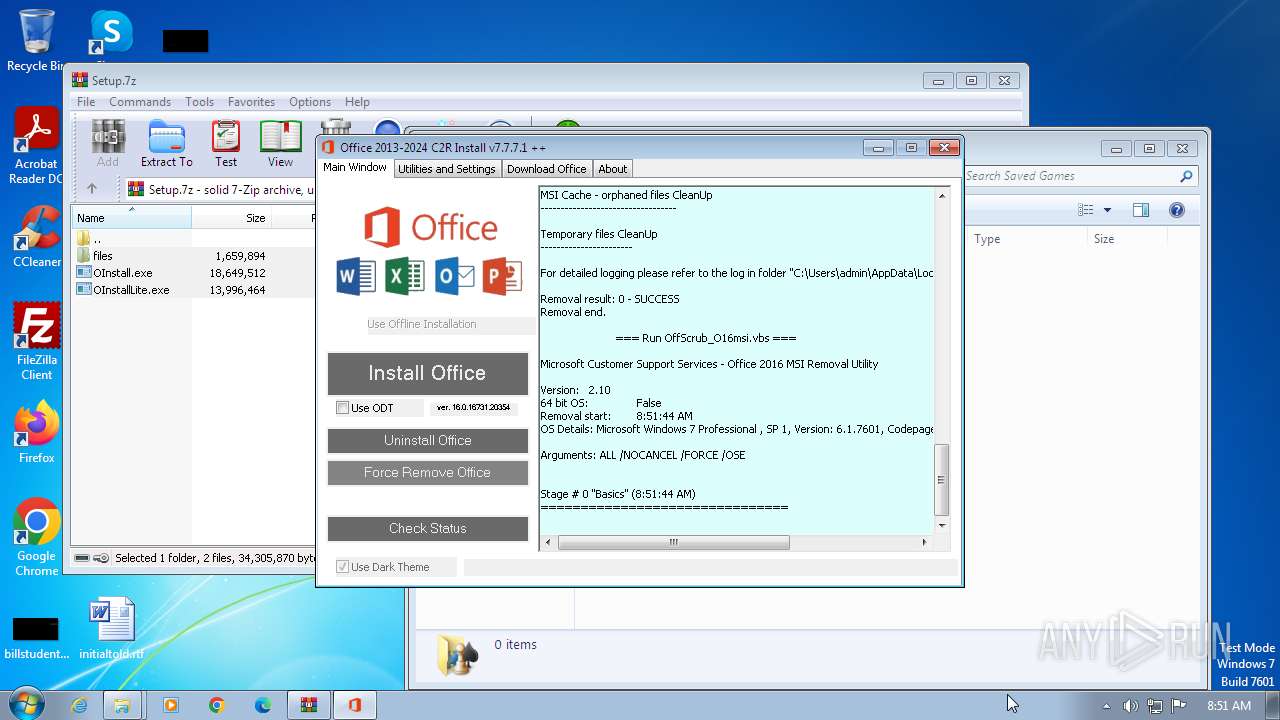
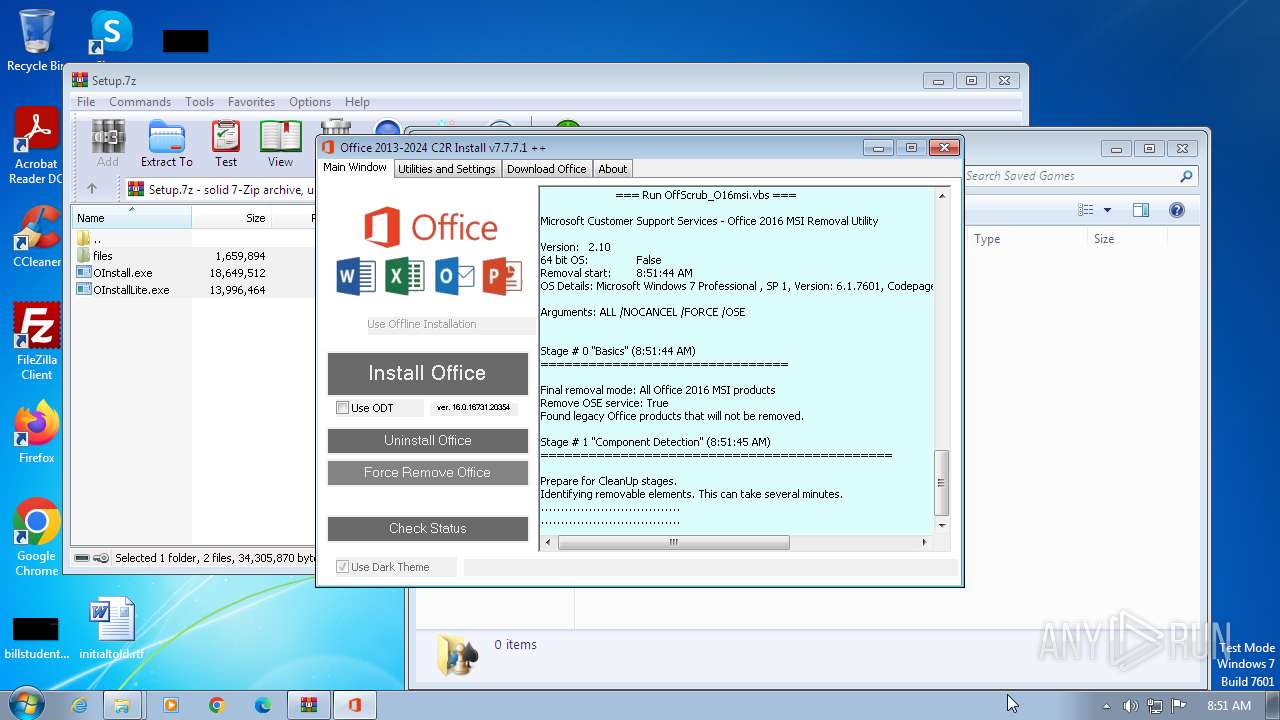
analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
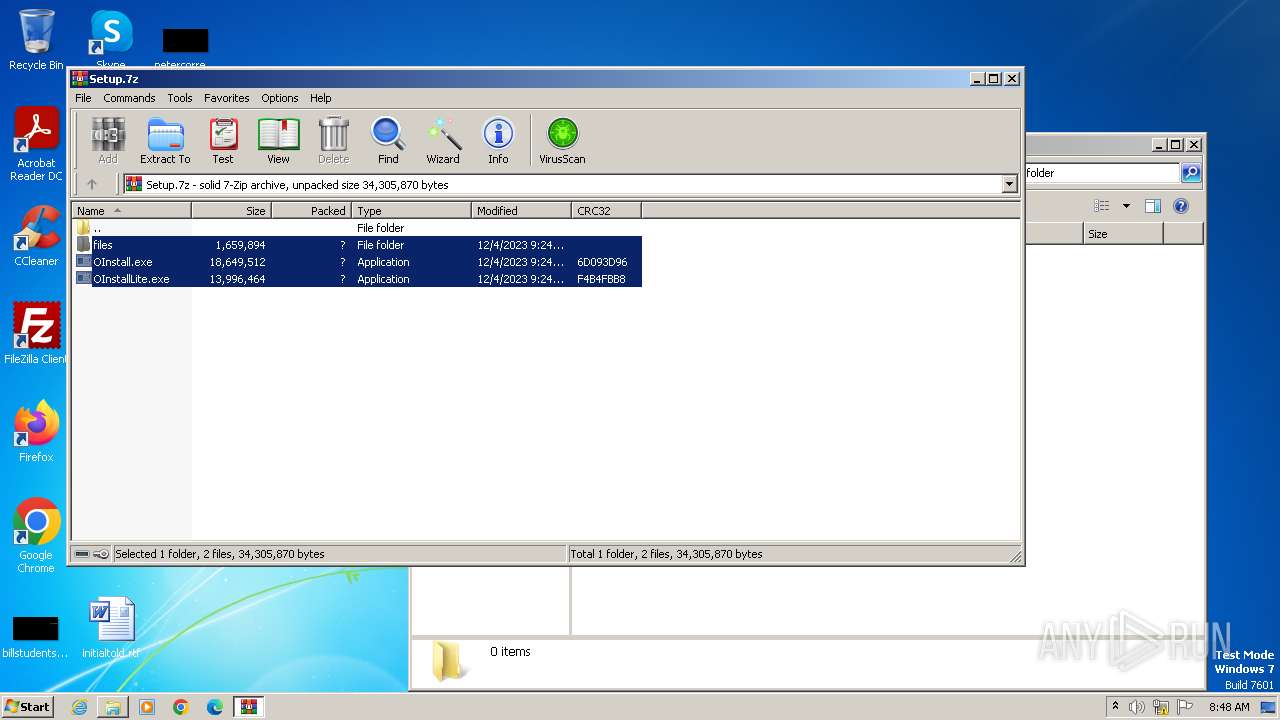
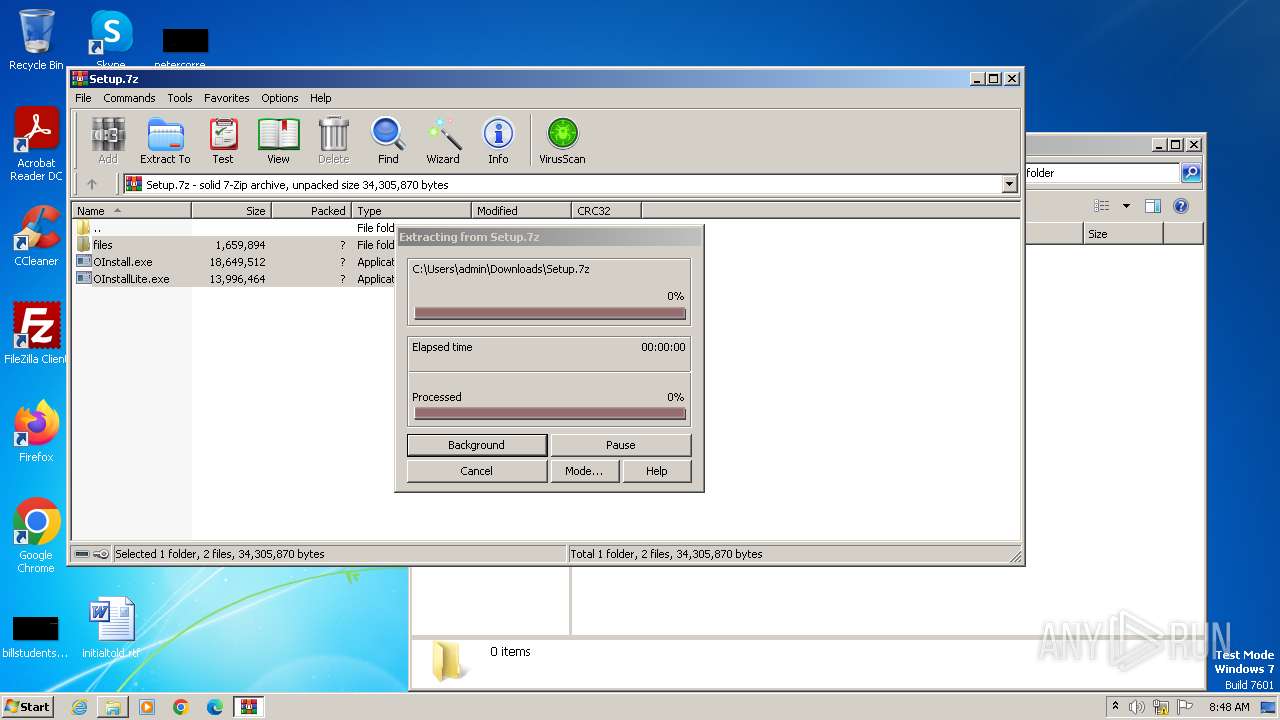
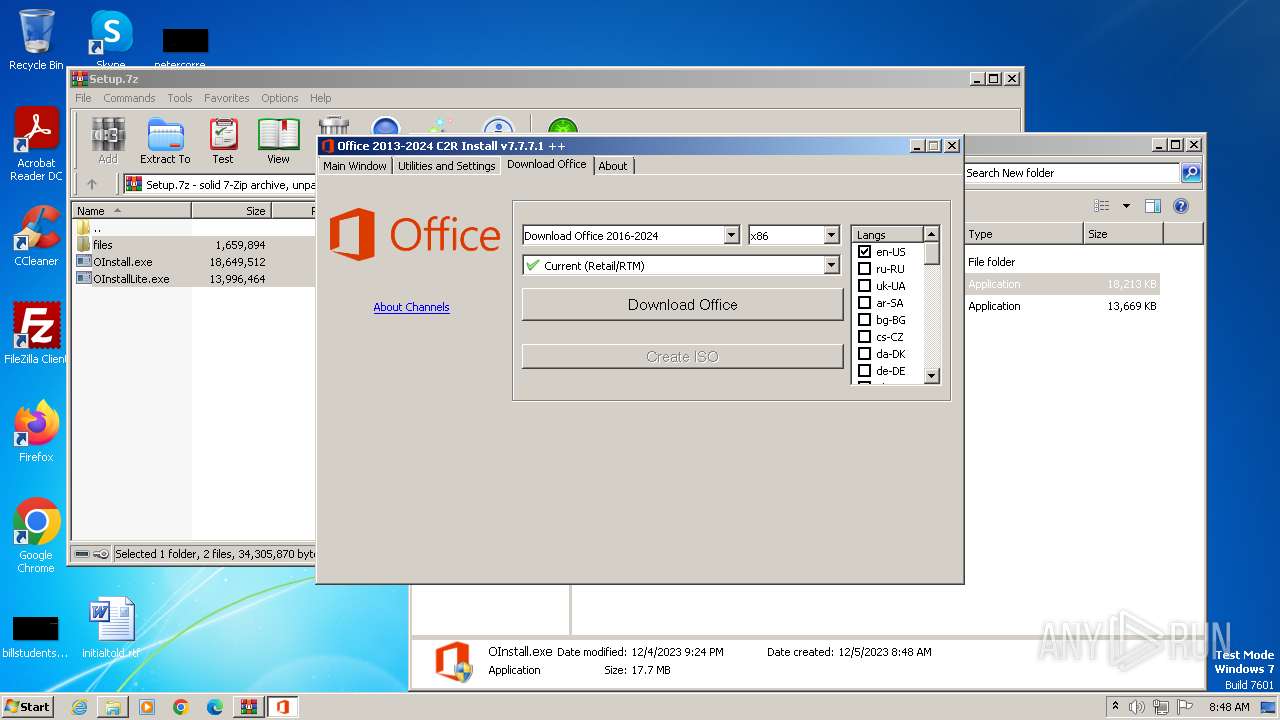
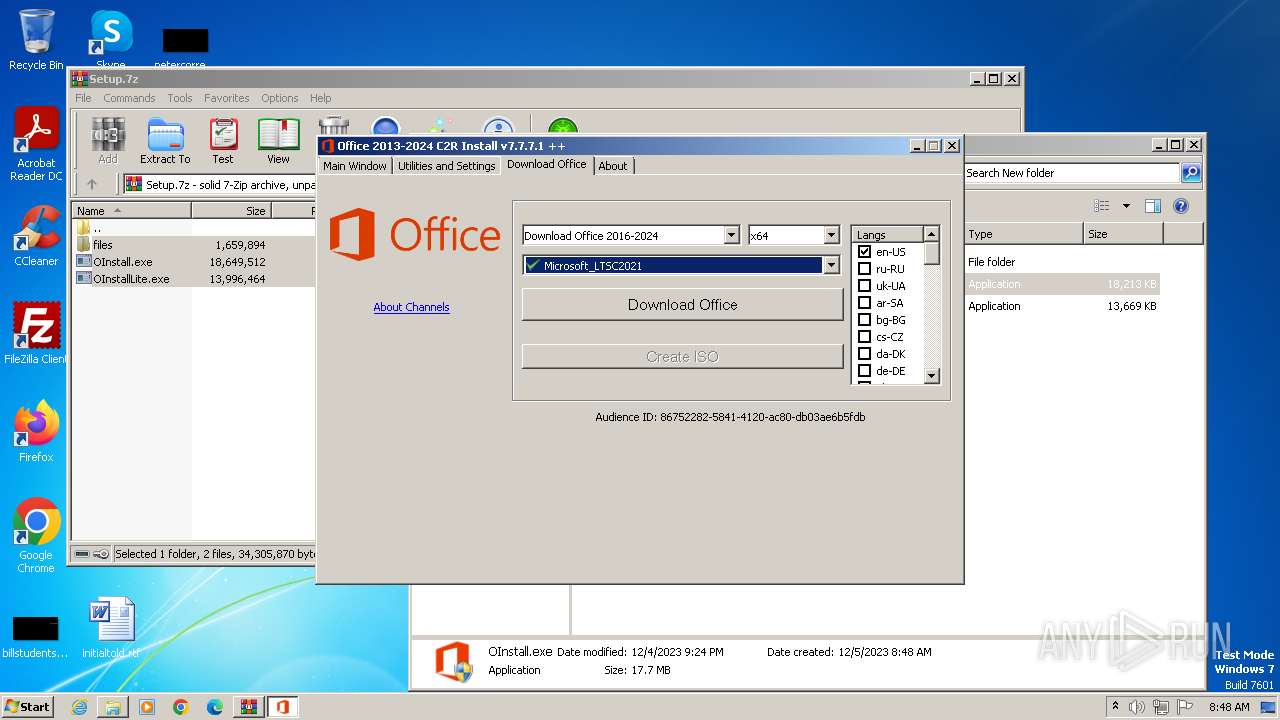
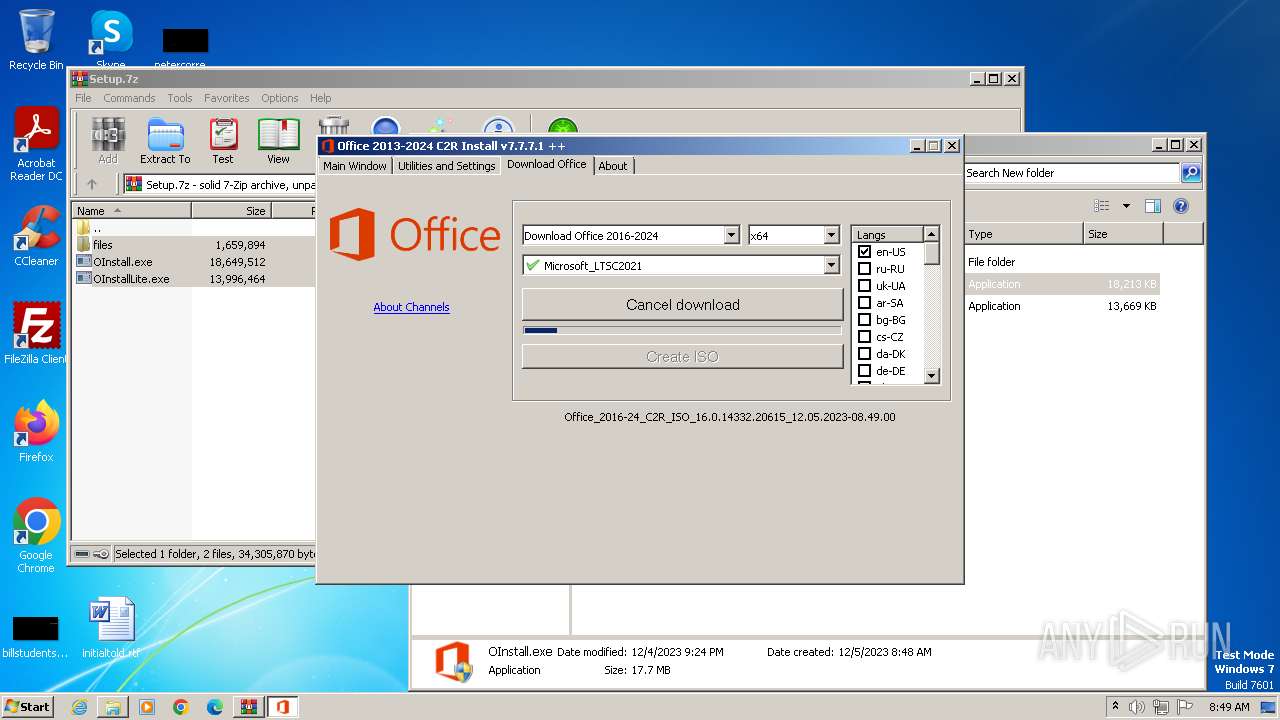
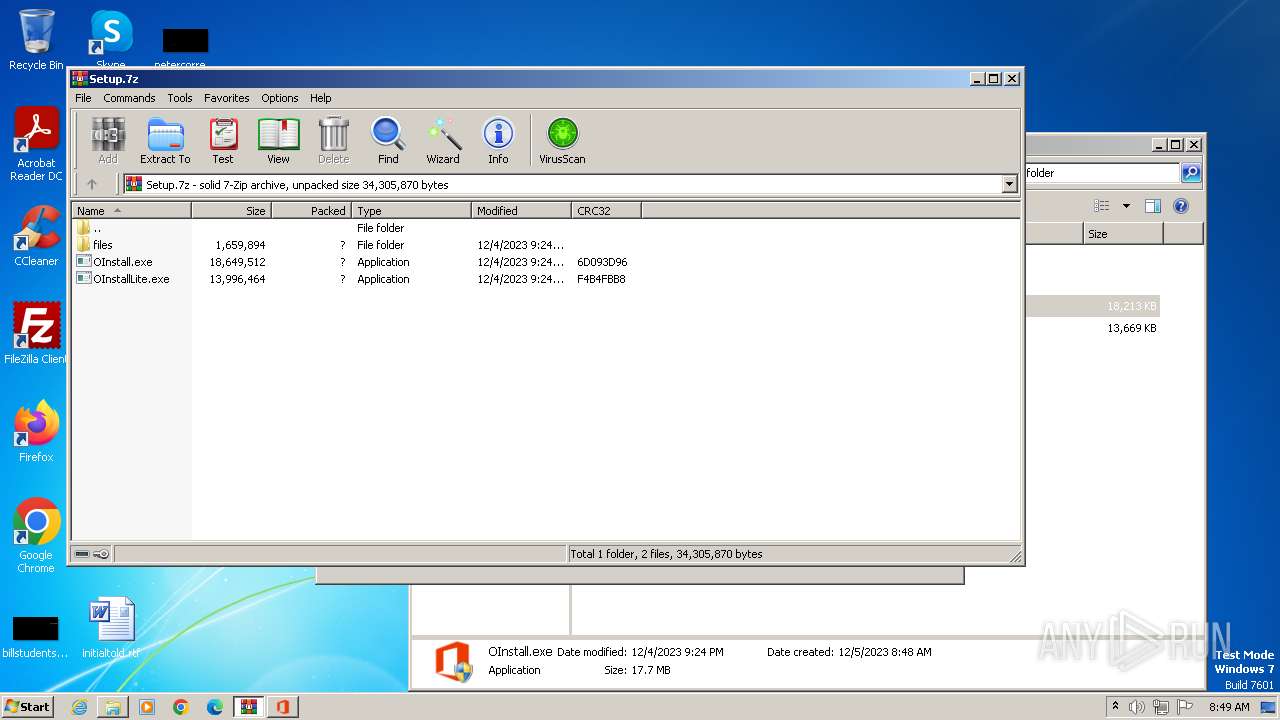
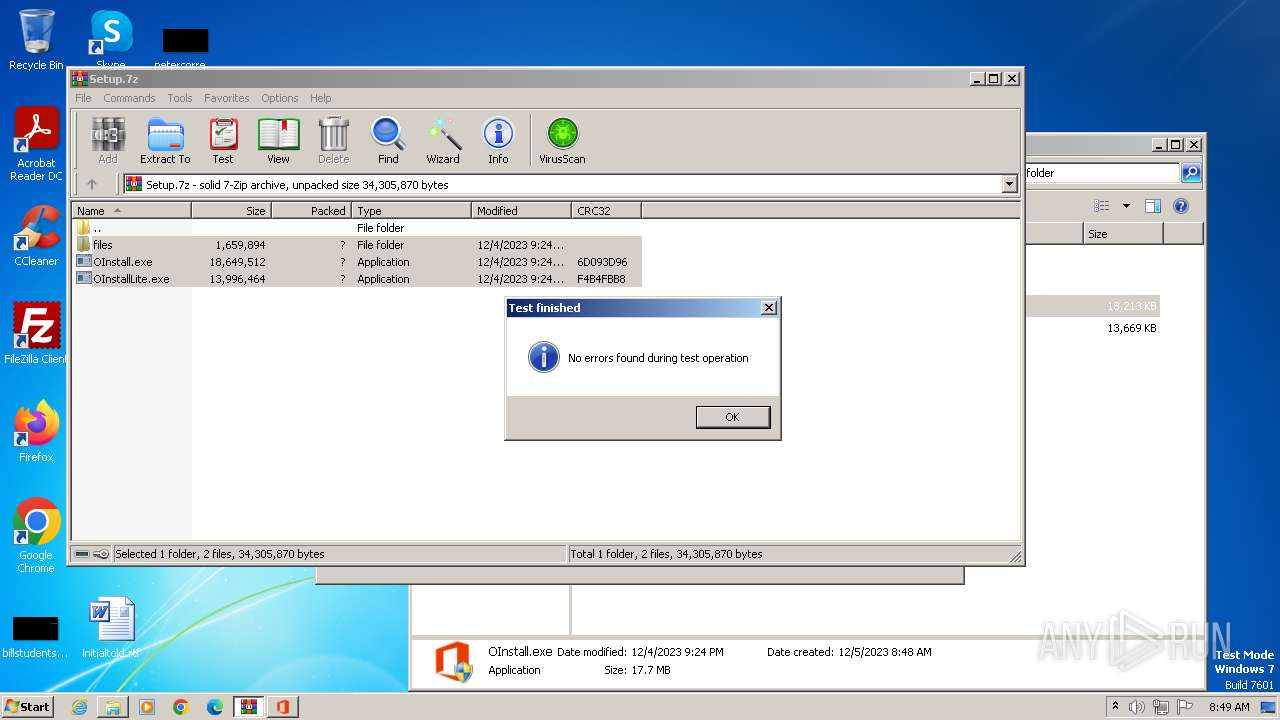
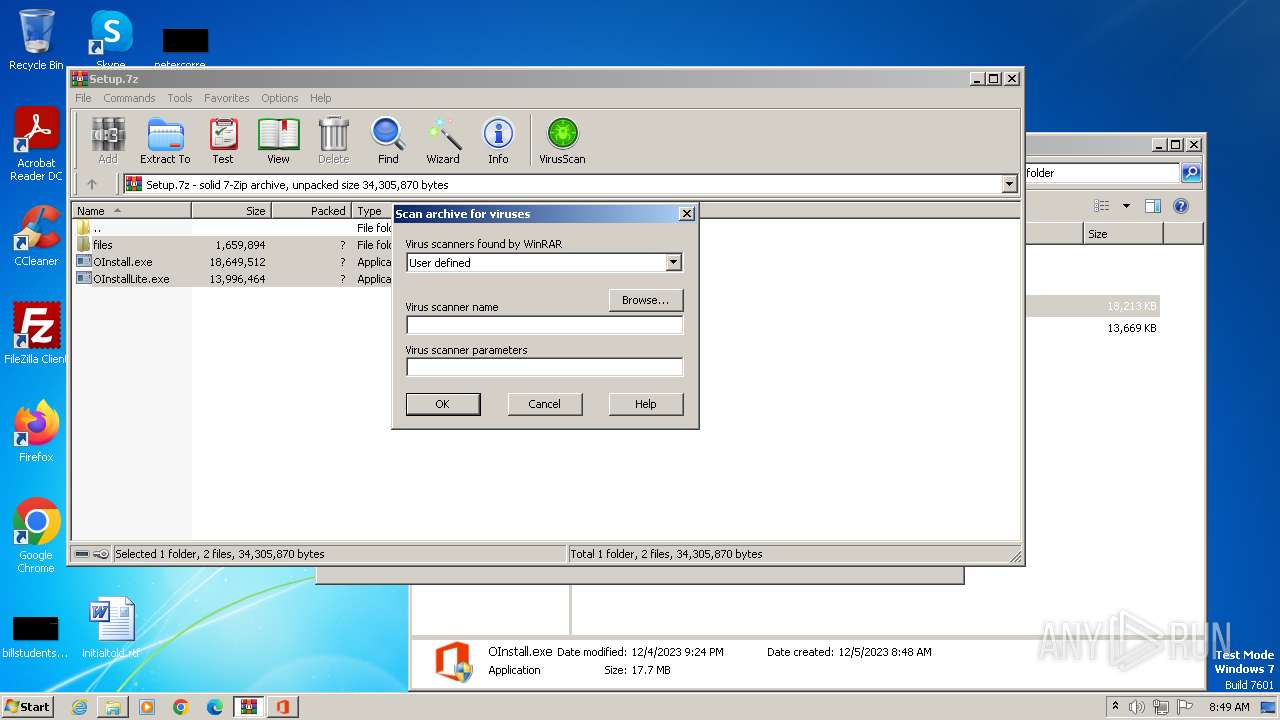
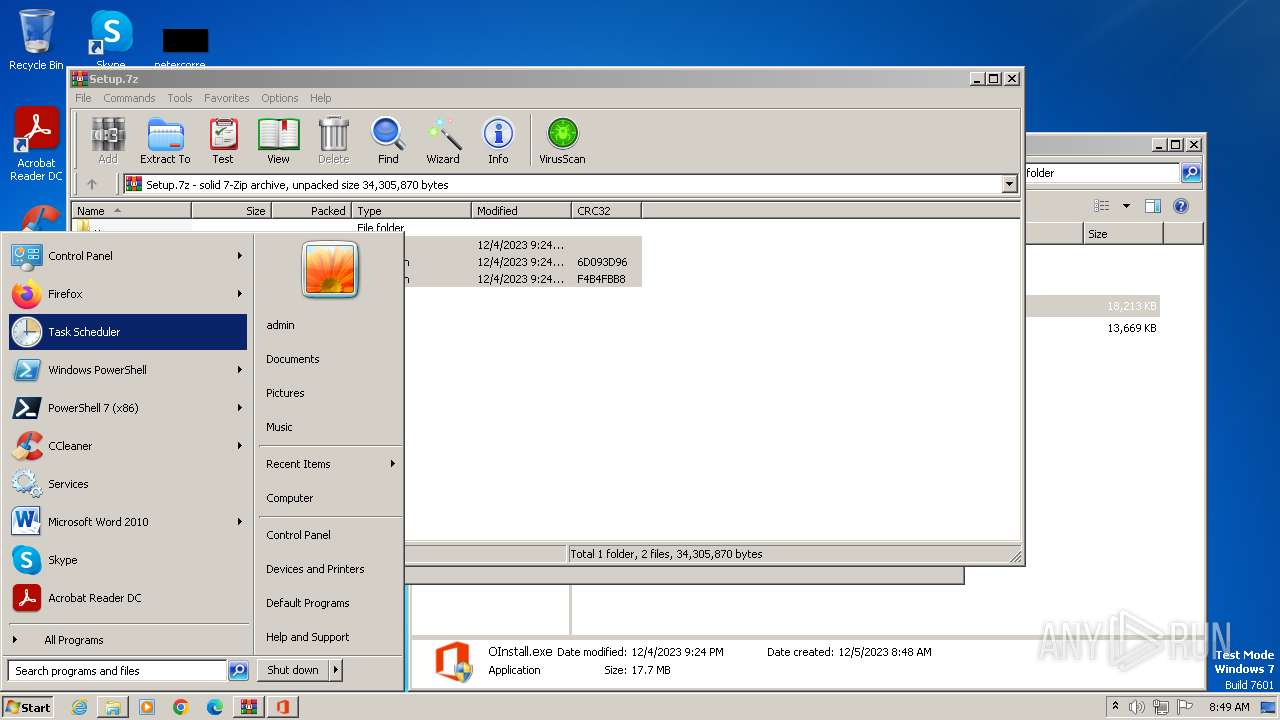
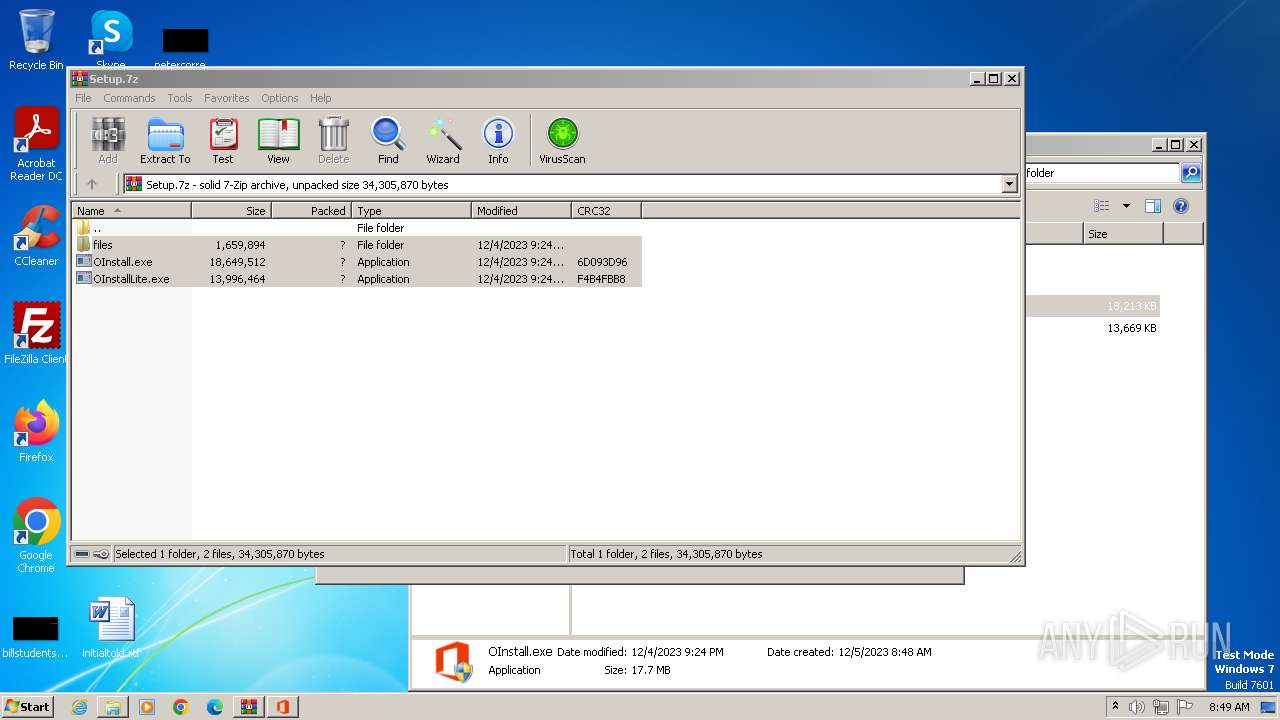
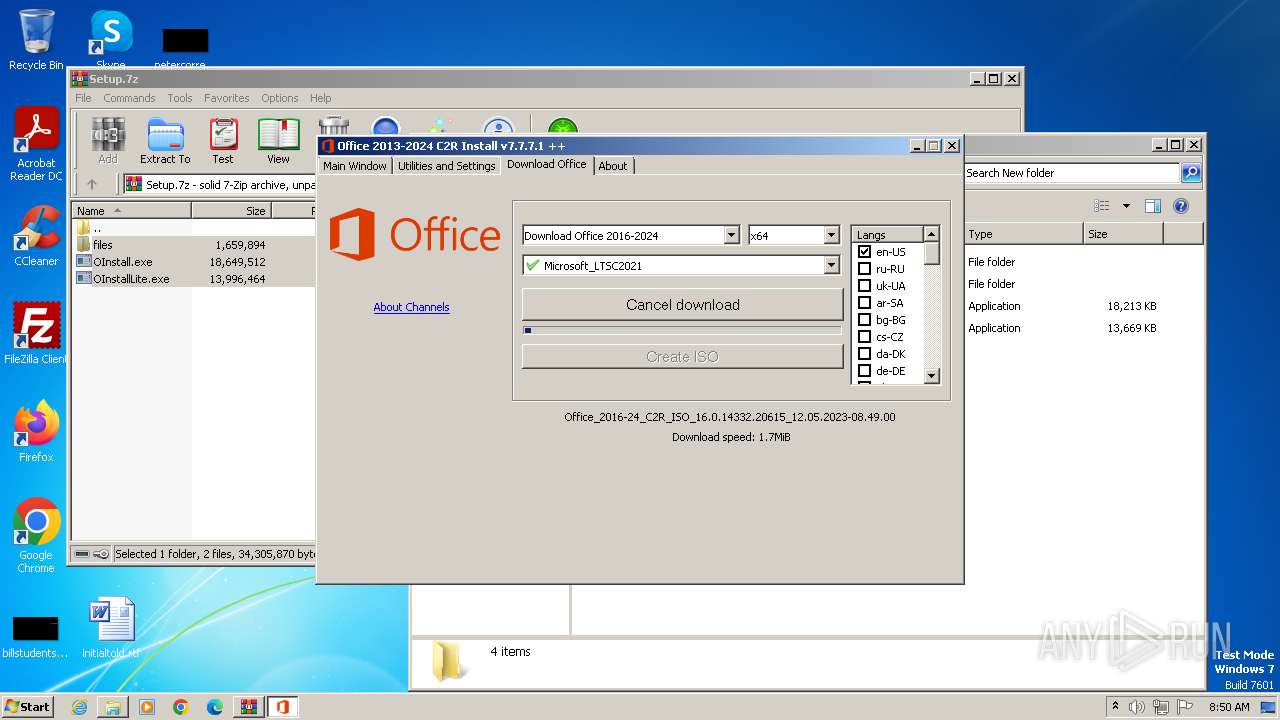
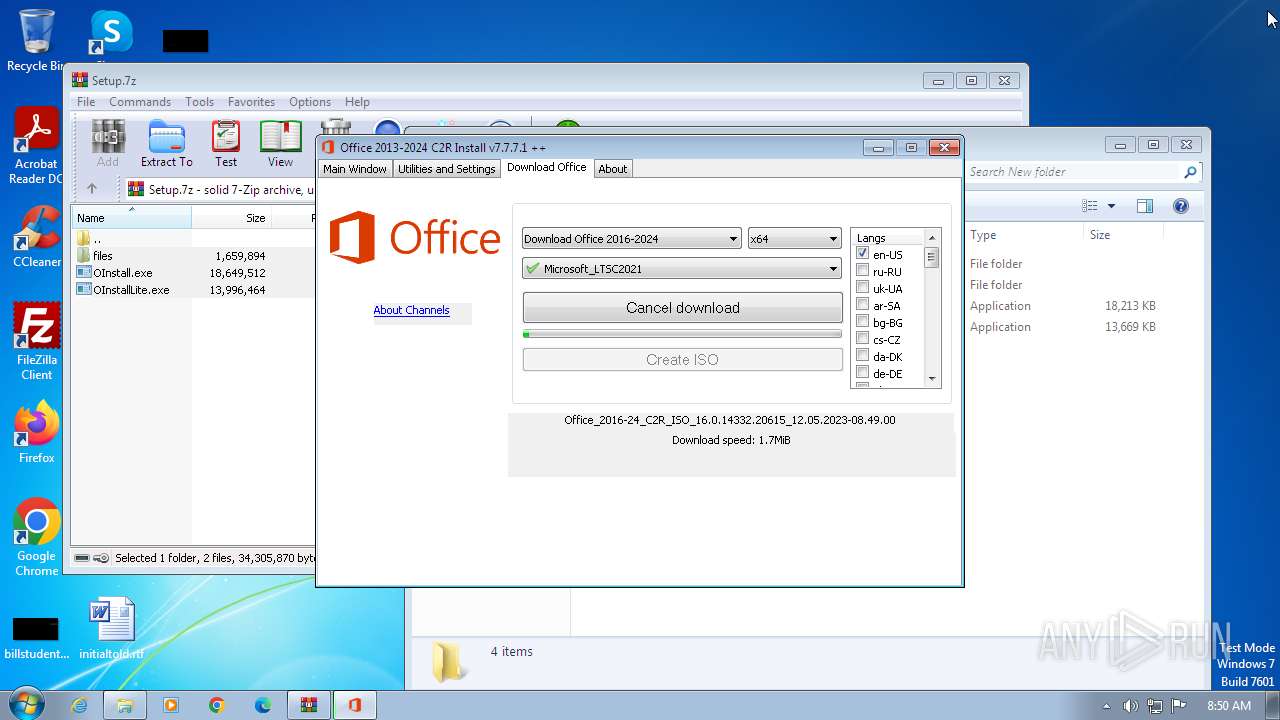
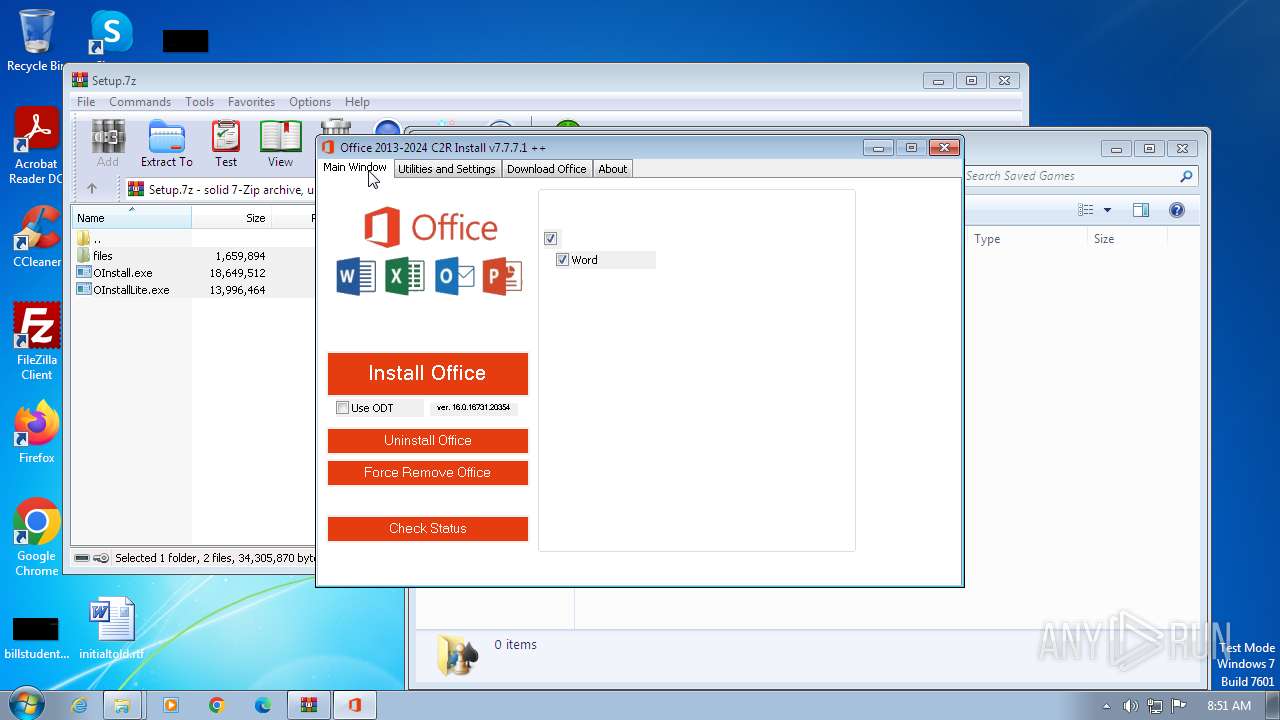
| File name: | Setup.7z |
| Full analysis: | https://app.any.run/tasks/bff04173-1844-4d07-8025-317cb08c021b |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2023, 08:47:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | F7D60A08A97CFFB0D403E5F16E489CF7 |
| SHA1: | 639F8091B98A7B6E1627FD5266EB58E3EE3FD36B |
| SHA256: | 0B44420C4C7433FDE00F1B4BC052EC0EFCAFA0C401618AFDAB8F6B9342ED7730 |
| SSDEEP: | 98304:UdNiMLb5x5mdCuyKCBrQUUE5HZeIk8glUrAe/xRz5A1fxERbNTge7R0xH9iYIezb:hbn7XFWjLZRaxcb8AAqO |
MALICIOUS
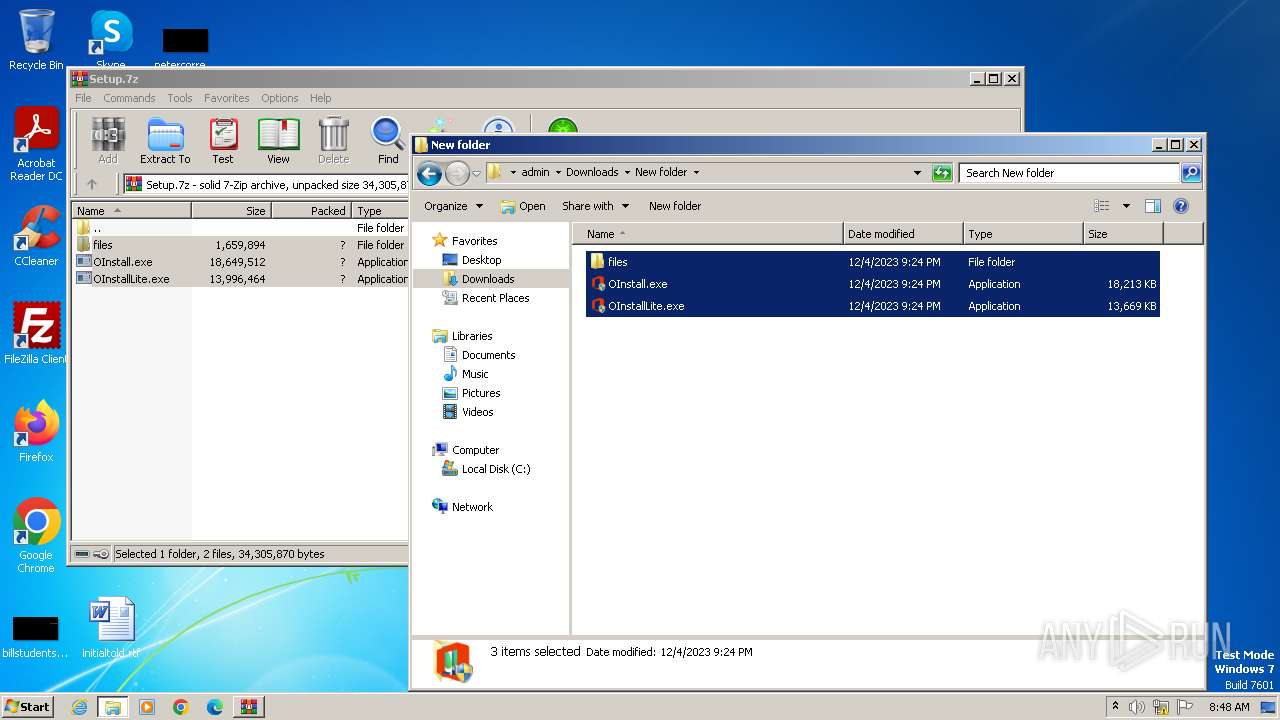
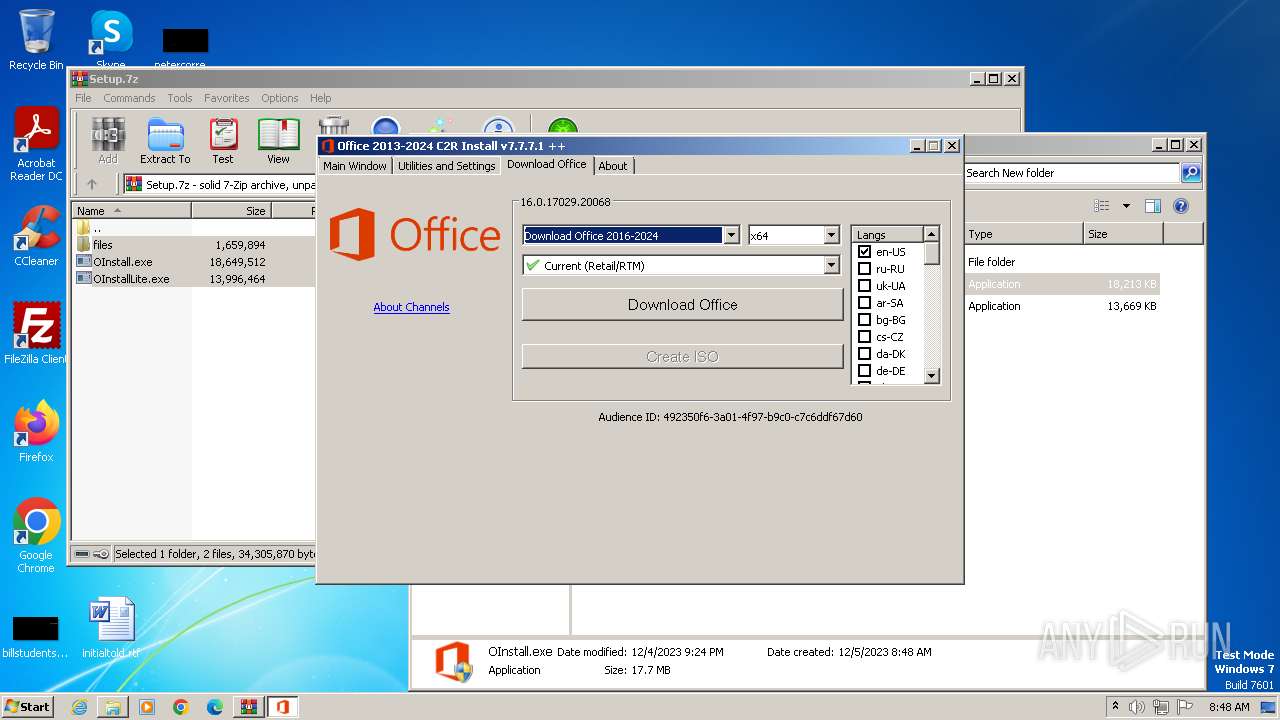
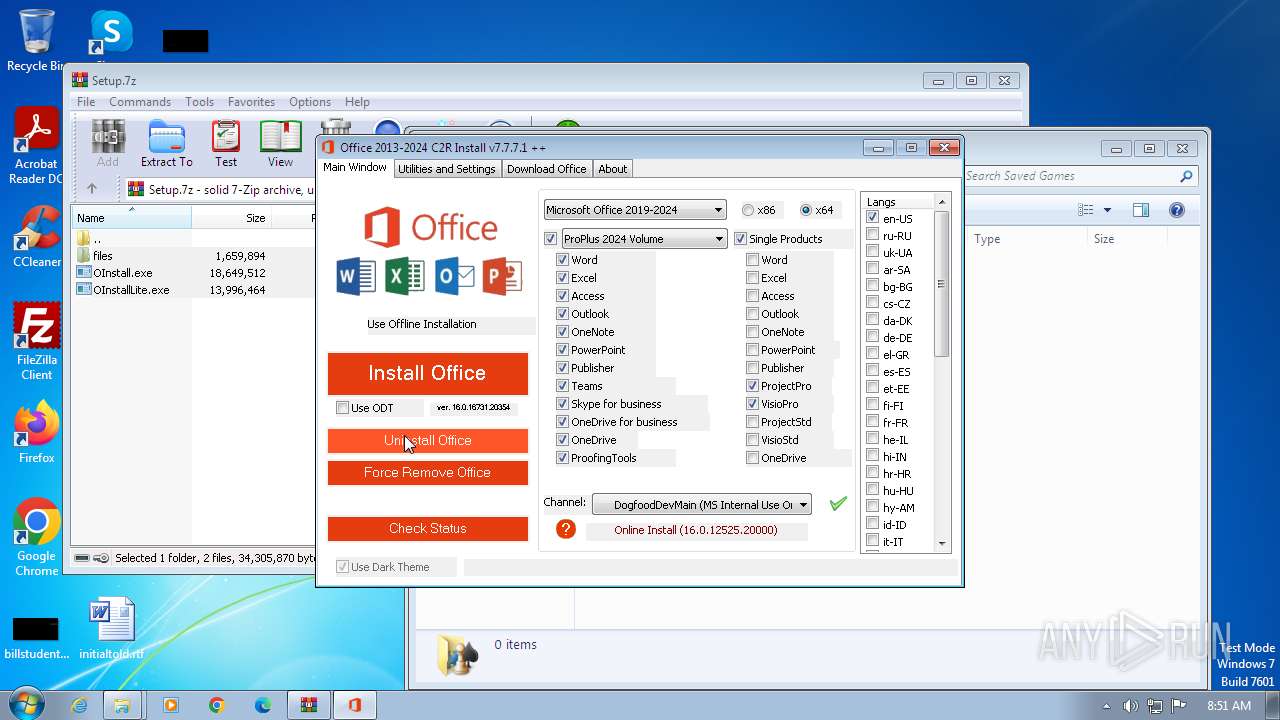
Drops the executable file immediately after the start
- OInstall.exe (PID: 3916)
- files.dat (PID: 2696)
Uses Task Scheduler to run other applications
- cscript.exe (PID: 3272)
Starts NET.EXE for service management
- cmd.exe (PID: 2792)
- net.exe (PID: 3780)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3060)
- OInstall.exe (PID: 3916)
- files.dat (PID: 2696)
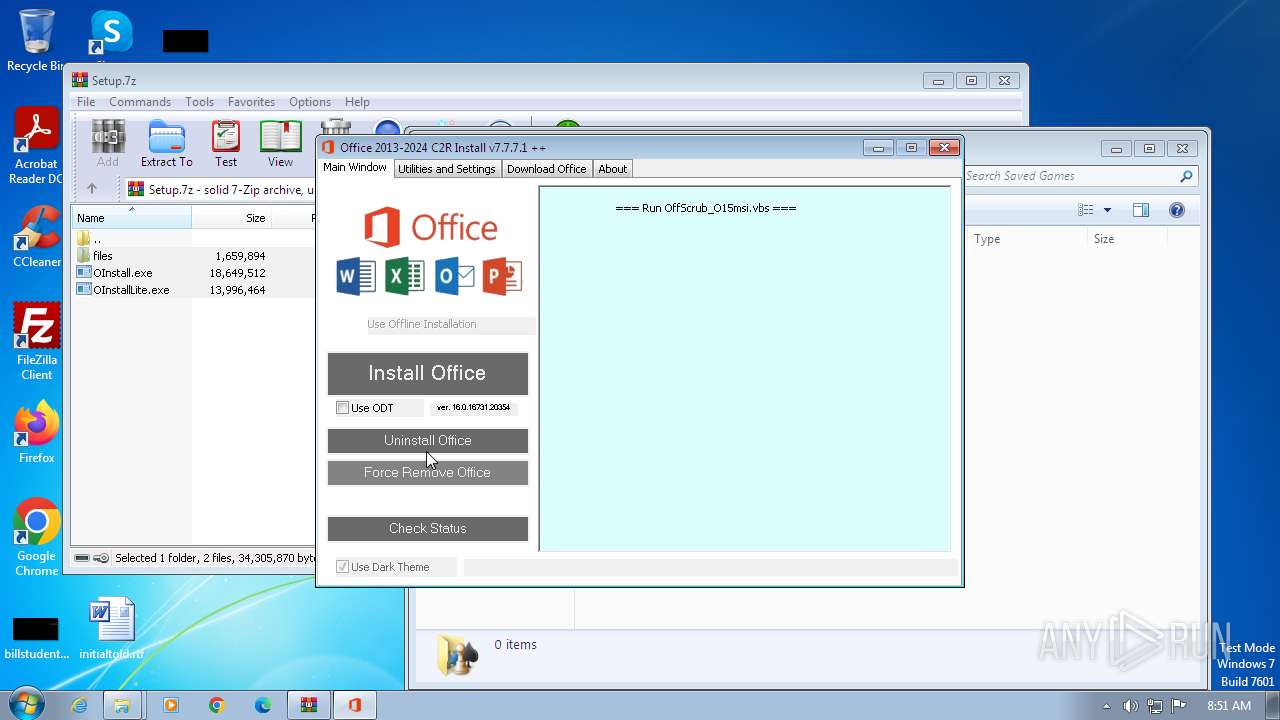
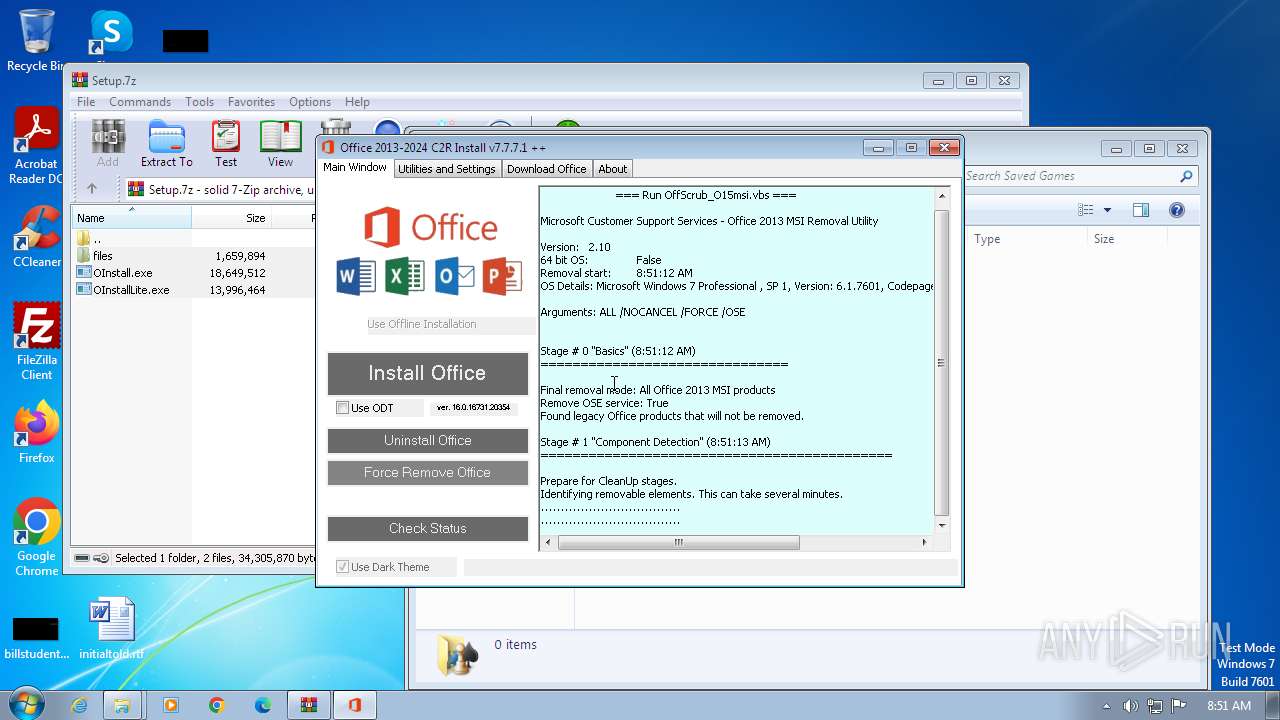
Uses REG/REGEDIT.EXE to modify registry
- OInstall.exe (PID: 3916)
Uses TASKKILL.EXE to kill process
- OInstall.exe (PID: 3916)
Starts CMD.EXE for commands execution
- OInstall.exe (PID: 3916)
- cscript.exe (PID: 3272)
Starts application with an unusual extension
- cmd.exe (PID: 3168)
Drops 7-zip archiver for unpacking
- OInstall.exe (PID: 3916)
The process drops C-runtime libraries
- files.dat (PID: 2696)
The process executes VB scripts
- cmd.exe (PID: 3228)
- cmd.exe (PID: 1004)
- cmd.exe (PID: 856)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 3728)
- aria2_oinstall.exe (PID: 3864)
- OInstall.exe (PID: 3916)
- aria2_oinstall.exe (PID: 3820)
- aria2_oinstall.exe (PID: 3576)
- sidebar.exe (PID: 4052)
Checks supported languages
- wmpnscfg.exe (PID: 3728)
- OInstall.exe (PID: 3916)
- aria2_oinstall.exe (PID: 3864)
- aria2_oinstall.exe (PID: 3576)
- aria2_oinstall.exe (PID: 3820)
- sidebar.exe (PID: 4052)
Manual execution by a user
- explorer.exe (PID: 1832)
- OInstall.exe (PID: 2548)
- OInstall.exe (PID: 3916)
- wmpnscfg.exe (PID: 3728)
- sidebar.exe (PID: 4052)
- control.exe (PID: 3412)
Reads Environment values
- OInstall.exe (PID: 3916)
Reads the machine GUID from the registry
- aria2_oinstall.exe (PID: 3864)
- aria2_oinstall.exe (PID: 3576)
- aria2_oinstall.exe (PID: 3820)
- sidebar.exe (PID: 4052)
Create files in a temporary directory
- aria2_oinstall.exe (PID: 3864)
- OInstall.exe (PID: 3916)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3060)
The executable file from the user directory is run by the CMD process
- aria2_oinstall.exe (PID: 3820)
- aria2_oinstall.exe (PID: 3576)
- files.dat (PID: 2696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
119
Monitored processes
43
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3060 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Setup.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1832 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
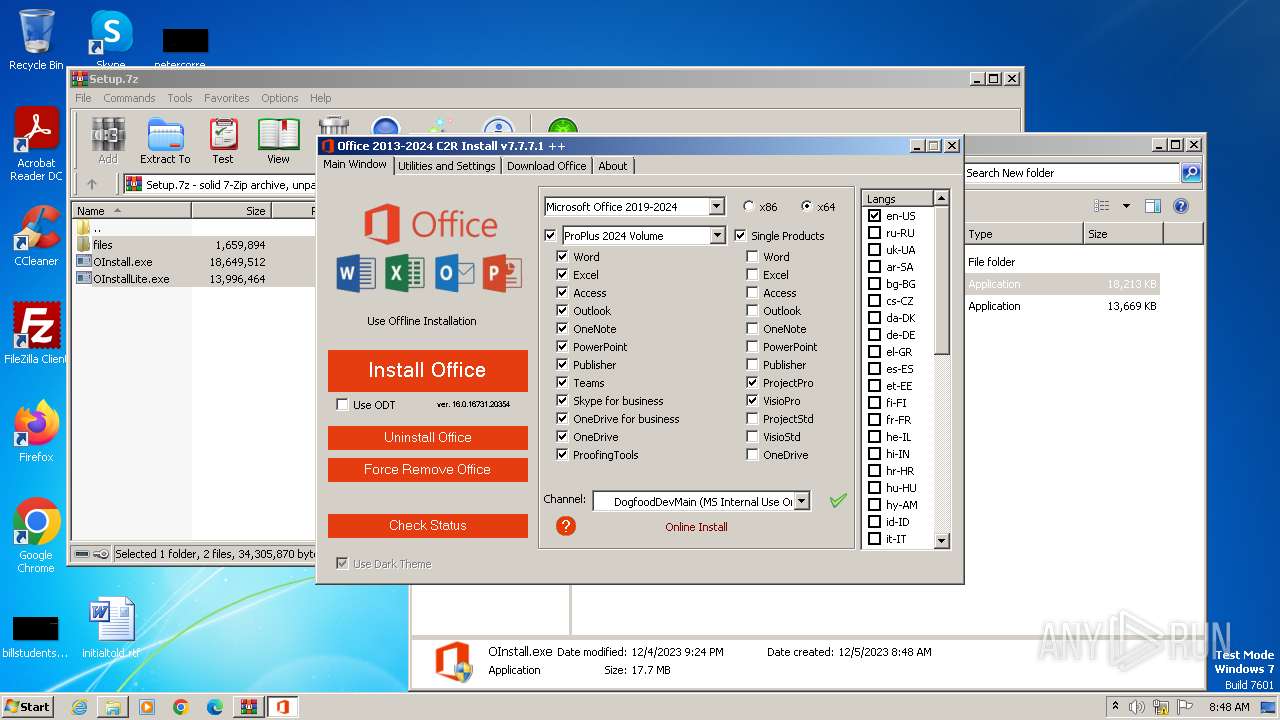
| 2548 | "C:\Users\admin\Downloads\New folder\OInstall.exe" | C:\Users\admin\Downloads\New folder\OInstall.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Office 2013-2024 C2R Install Exit code: 3221226540 Modules
| |||||||||||||||
| 3916 | "C:\Users\admin\Downloads\New folder\OInstall.exe" | C:\Users\admin\Downloads\New folder\OInstall.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Office 2013-2024 C2R Install Modules
| |||||||||||||||
| 1004 | "C:\Windows\System32\reg.exe" add "HKLM\SOFTWARE\Microsoft\Windows Script Host\Settings" /v Enabled /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3864 | "C:\Users\admin\AppData\Local\Temp\aria2_oinstall.exe" https://mrodevicemgr.officeapps.live.com/mrodevicemgrsvc/api/v2/C2RReleaseData -over.txt | C:\Users\admin\AppData\Local\Temp\aria2_oinstall.exe | OInstall.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3728 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3228 | "taskkill.exe" /t /f /IM aria2_oinstall.exe | C:\Windows\System32\taskkill.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
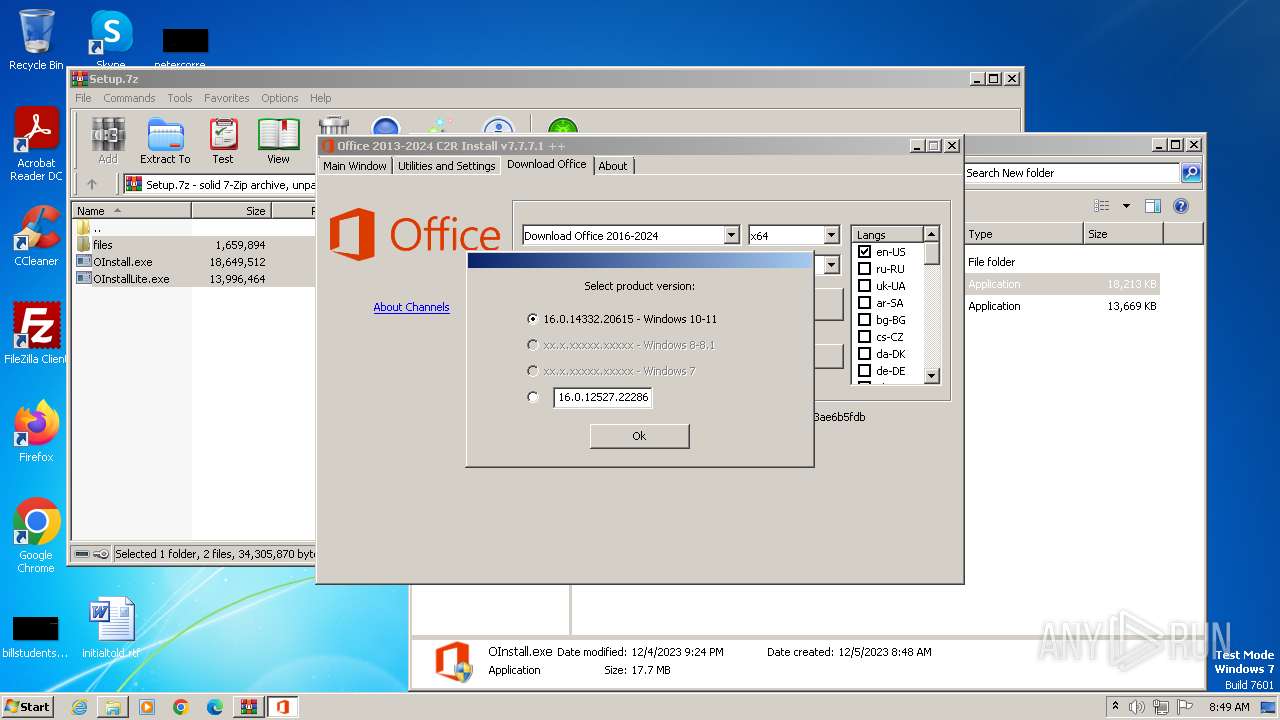
| 1420 | "C:\Windows\System32\cmd.exe" /D /c "C:\Users\admin\Downloads\New folder\files\aria2_oinstall.exe" --console-log-level=info --check-certificate=false -x16 -s16 -j1 -c -R -Ztrue -m60 --retry-wait=5 -dOffice\Data http://officecdn.microsoft.com/db/86752282-5841-4120-ac80-db03ae6b5fdb/Office/Data/v64.cab http://officecdn.microsoft.com/db/86752282-5841-4120-ac80-db03ae6b5fdb/Office/Data/v64_16.0.14332.20615.cab | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3576 | "C:\Users\admin\Downloads\New folder\files\aria2_oinstall.exe" --console-log-level=info --check-certificate=false -x16 -s16 -j1 -c -R -Ztrue -m60 --retry-wait=5 -dOffice\Data http://officecdn.microsoft.com/db/86752282-5841-4120-ac80-db03ae6b5fdb/Office/Data/v64.cab http://officecdn.microsoft.com/db/86752282-5841-4120-ac80-db03ae6b5fdb/Office/Data/v64_16.0.14332.20615.cab | C:\Users\admin\Downloads\New folder\files\aria2_oinstall.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
2 891
Read events
2 868
Write events
23
Delete events
0
Modification events
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3916) OInstall.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3916) OInstall.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
Executable files
16
Suspicious files
50
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3060.8522\files\Configure.xml | text | |
MD5:3DC4C6DDB4B867195B60960CC0E468CC | SHA256:10EB1A8B624052B725536B687FE6B30DB4DDBAD961A742D8DAA1F3B689E0BBB7 | |||
| 3060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3060.8522\files\x64\cleanospp.exe | executable | |
MD5:D3467CB7B83B654C2D05407DC7BA2360 | SHA256:EDF85F4E2EF1A427B34265A22F261D664EC78DE90C3B5DA4174EF28558C8522A | |||
| 3060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3060.8522\files\x86\cleanospp.exe | executable | |
MD5:98821A7A5737D656633D10A3AFB724BD | SHA256:04BA4487F95290E0B0557B44300C18F637FBAF0872EE96E3111013B8A1539F25 | |||
| 3916 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\aria2_oinstall.exe | executable | |
MD5:B95DBDE252CC8EA490E1D9D04EC5FE0D | SHA256:0AE98794B3523634B0AF362D6F8C04A9BBD32AEDA959B72CA0E7FC24E84D2A66 | |||
| 3916 | OInstall.exe | C:\Users\admin\Downloads\New folder\files\aria2_oinstall.exe | executable | |
MD5:B95DBDE252CC8EA490E1D9D04EC5FE0D | SHA256:0AE98794B3523634B0AF362D6F8C04A9BBD32AEDA959B72CA0E7FC24E84D2A66 | |||
| 3060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3060.8522\files\x86\msvcr100.dll | executable | |
MD5:BF38660A9125935658CFA3E53FDC7D65 | SHA256:60C06E0FA4449314DA3A0A87C1A9D9577DF99226F943637E06F61188E5862EFA | |||
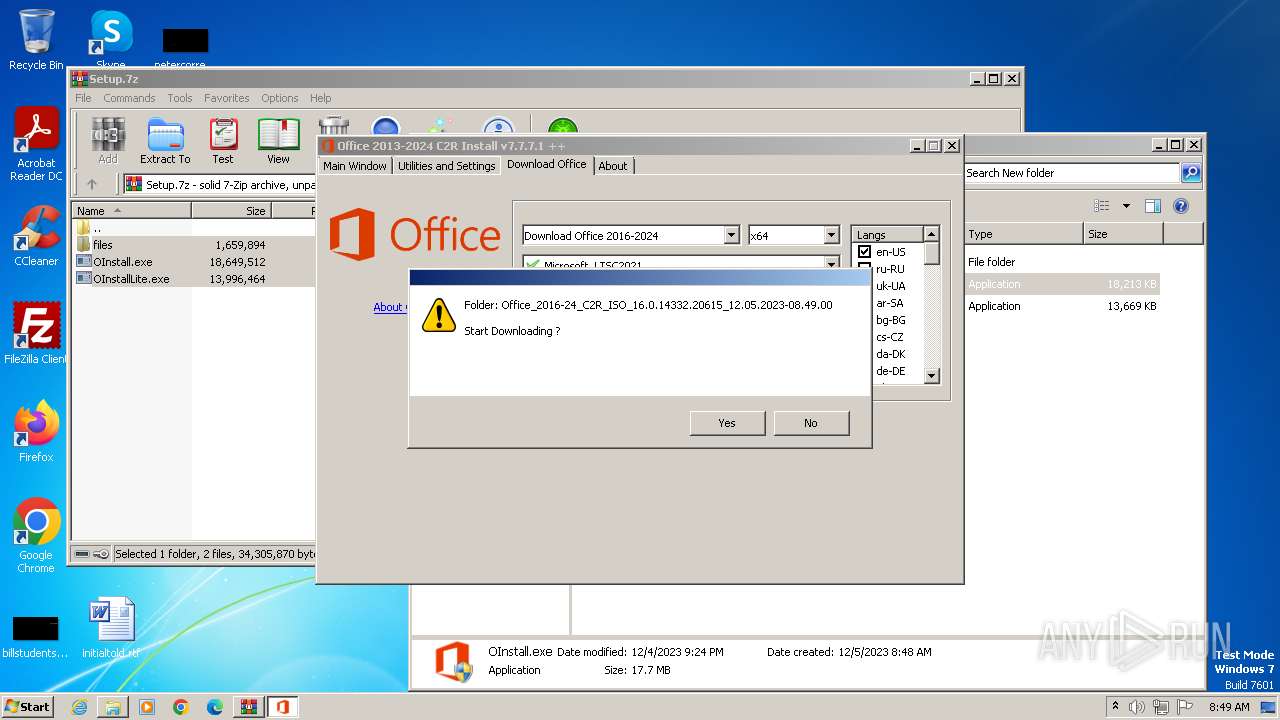
| 3916 | OInstall.exe | C:\Users\admin\Downloads\New folder\Office_2016-24_C2R_ISO_16.0.14332.20615_12.05.2023-08.49.00\Office\Data\branch.txt | text | |
MD5:D112EA48550735B974EC9759871A797D | SHA256:49C39262980F40EFBC387E6DBCBA5899CD58D0853FADC6ECA76C28E0B3151831 | |||
| 3060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3060.8522\files\x64\msvcr100.dll | executable | |
MD5:DF3CA8D16BDED6A54977B30E66864D33 | SHA256:1D1A1AE540BA132F998D60D3622F0297B6E86AE399332C3B47462D7C0F560A36 | |||
| 3916 | OInstall.exe | C:\Users\admin\Downloads\New folder\Office_2016-24_C2R_ISO_16.0.14332.20615_12.05.2023-08.49.00\tmp.$$ | text | |
MD5:098F6BCD4621D373CADE4E832627B4F6 | SHA256:9F86D081884C7D659A2FEAA0C55AD015A3BF4F1B2B0B822CD15D6C15B0F00A08 | |||
| 3916 | OInstall.exe | C:\Users\admin\Downloads\New folder\files\Configure.xml | text | |
MD5:9584B9C567B3F9F20DEB576028CD74A2 | SHA256:B7B6A9C43CD1CD9B77DE305411EEF95BDB37F5D613FC7B62FC488B2CF413289A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
39
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3820 | aria2_oinstall.exe | GET | — | 23.48.23.45:80 | http://officecdn.microsoft.com/db/86752282-5841-4120-ac80-db03ae6b5fdb/Office/Data/16.0.14332.20615/stream.x64.en-US.proof.dat | unknown | — | — | unknown |
3820 | aria2_oinstall.exe | GET | 200 | 23.48.23.45:80 | http://officecdn.microsoft.com/db/86752282-5841-4120-ac80-db03ae6b5fdb/Office/Data/16.0.14332.20615/stream.x64.en-US.dat.cat | unknown | binary | 126 Kb | unknown |
3820 | aria2_oinstall.exe | GET | — | 23.48.23.45:80 | http://officecdn.microsoft.com/db/86752282-5841-4120-ac80-db03ae6b5fdb/Office/Data/16.0.14332.20615/stream.x64.x-none.dat | unknown | — | — | unknown |
3576 | aria2_oinstall.exe | GET | 200 | 23.48.23.45:80 | http://officecdn.microsoft.com/db/86752282-5841-4120-ac80-db03ae6b5fdb/Office/Data/v64_16.0.14332.20615.cab | unknown | compressed | 10.7 Kb | unknown |
3820 | aria2_oinstall.exe | GET | 200 | 23.48.23.45:80 | http://officecdn.microsoft.com/db/86752282-5841-4120-ac80-db03ae6b5fdb/Office/Data/16.0.14332.20615/i640.cab.cat | unknown | binary | 31.3 Kb | unknown |
3820 | aria2_oinstall.exe | GET | — | 23.48.23.45:80 | http://officecdn.microsoft.com/db/86752282-5841-4120-ac80-db03ae6b5fdb/Office/Data/16.0.14332.20615/stream.x64.en-US.dat | unknown | — | — | unknown |
484 | lsass.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
3820 | aria2_oinstall.exe | GET | 200 | 23.48.23.45:80 | http://officecdn.microsoft.com/db/86752282-5841-4120-ac80-db03ae6b5fdb/Office/Data/16.0.14332.20615/sp641033.cab | unknown | compressed | 96.4 Kb | unknown |
3820 | aria2_oinstall.exe | GET | 200 | 23.48.23.45:80 | http://officecdn.microsoft.com/db/86752282-5841-4120-ac80-db03ae6b5fdb/Office/Data/16.0.14332.20615/stream.x64.en-US.proof.dat.cat | unknown | binary | 13.6 Kb | unknown |
484 | lsass.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?440741f4bd306e5a | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3864 | aria2_oinstall.exe | 52.109.89.117:443 | mrodevicemgr.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
484 | lsass.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
484 | lsass.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3576 | aria2_oinstall.exe | 23.48.23.45:80 | officecdn.microsoft.com | Akamai International B.V. | DE | unknown |
3820 | aria2_oinstall.exe | 23.48.23.45:80 | officecdn.microsoft.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mrodevicemgr.officeapps.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officecdn.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3576 | aria2_oinstall.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
3576 | aria2_oinstall.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
3820 | aria2_oinstall.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
3820 | aria2_oinstall.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
3820 | aria2_oinstall.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
3820 | aria2_oinstall.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
3820 | aria2_oinstall.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
3820 | aria2_oinstall.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
3820 | aria2_oinstall.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
3820 | aria2_oinstall.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |